Creating a user¶
Warning
Data model objects: safes, users, servers, accounts and listeners are replicated within the cluster and object instances must not be added on each node. In case the replication mechanism fails to copy objects to other nodes, contact technical support department.
Warning
When creating a User object for MySQL connections, please note that Fudo Enterprise does not support the MySQL server caching_sha2_password plugin. The supported MySQL plugins are mysql_native_password and mysql_old_password. To ensure compatibility, server plugin should be set to mysql_native_password in /etc/mysql/mysql.conf.d/mysqld.cnf file, and a User object should be created with mysql_native_password plugin.
To create a user definition, follow the instructions below.
- Click + icon next to the tab of the sub-section, or
- Select > and then click .
- Enter user name.
Note
- While there can be more than one user with the same Name, the Name and domain combination must be unique.
- The Name field is not case sensitive.
Warning
It’s not allowed to include % and # characters within the usernames.
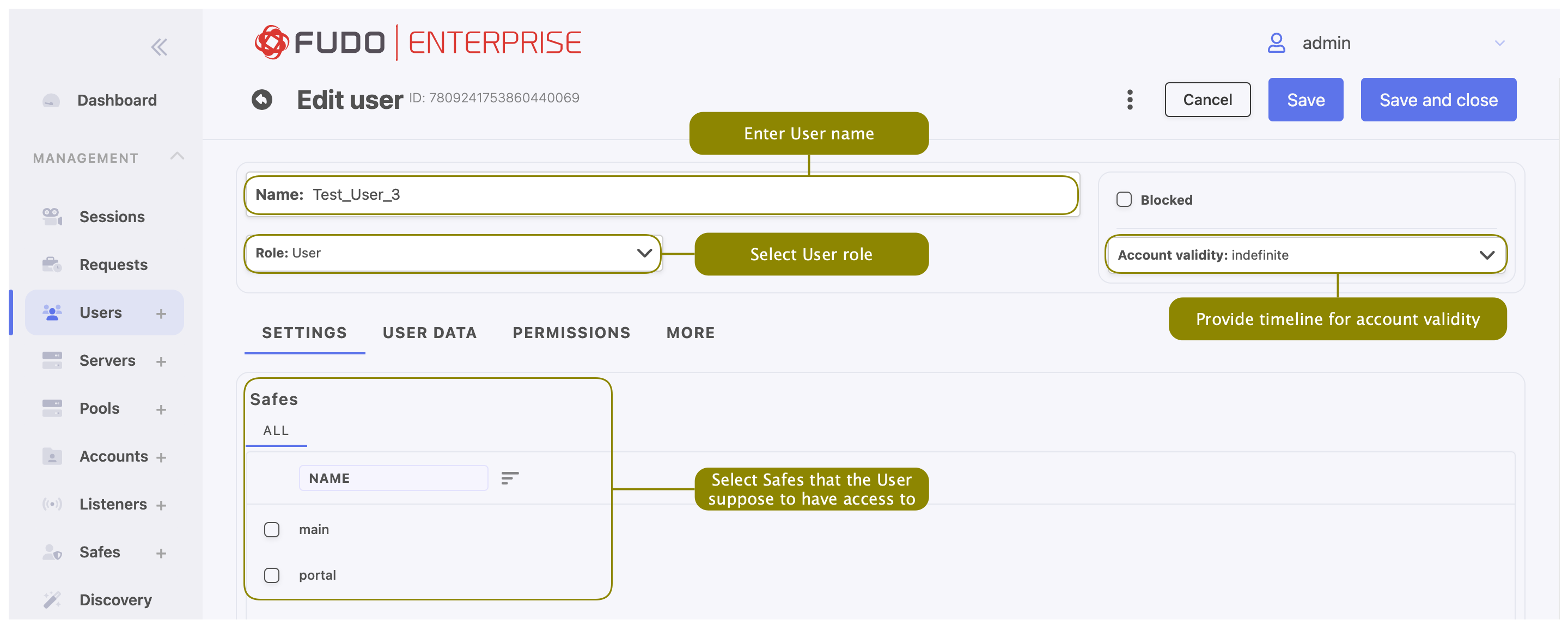
- From the Role drop-down list select user’s role, which will determine the access rights.
Note
Access rights restrictions also apply to API interface access.
| Role | Access rights |
|---|---|
| user |
|
| service |
|
| operator |
|
| admin |
|
| superadmin |
|
- Select the Blocked option to prevent user from accessing servers and resources monitored by Fudo Enterprise.
- Define account’s validity period.
- In the Settings tab, in the Safes field, select desired safes to grant access to.
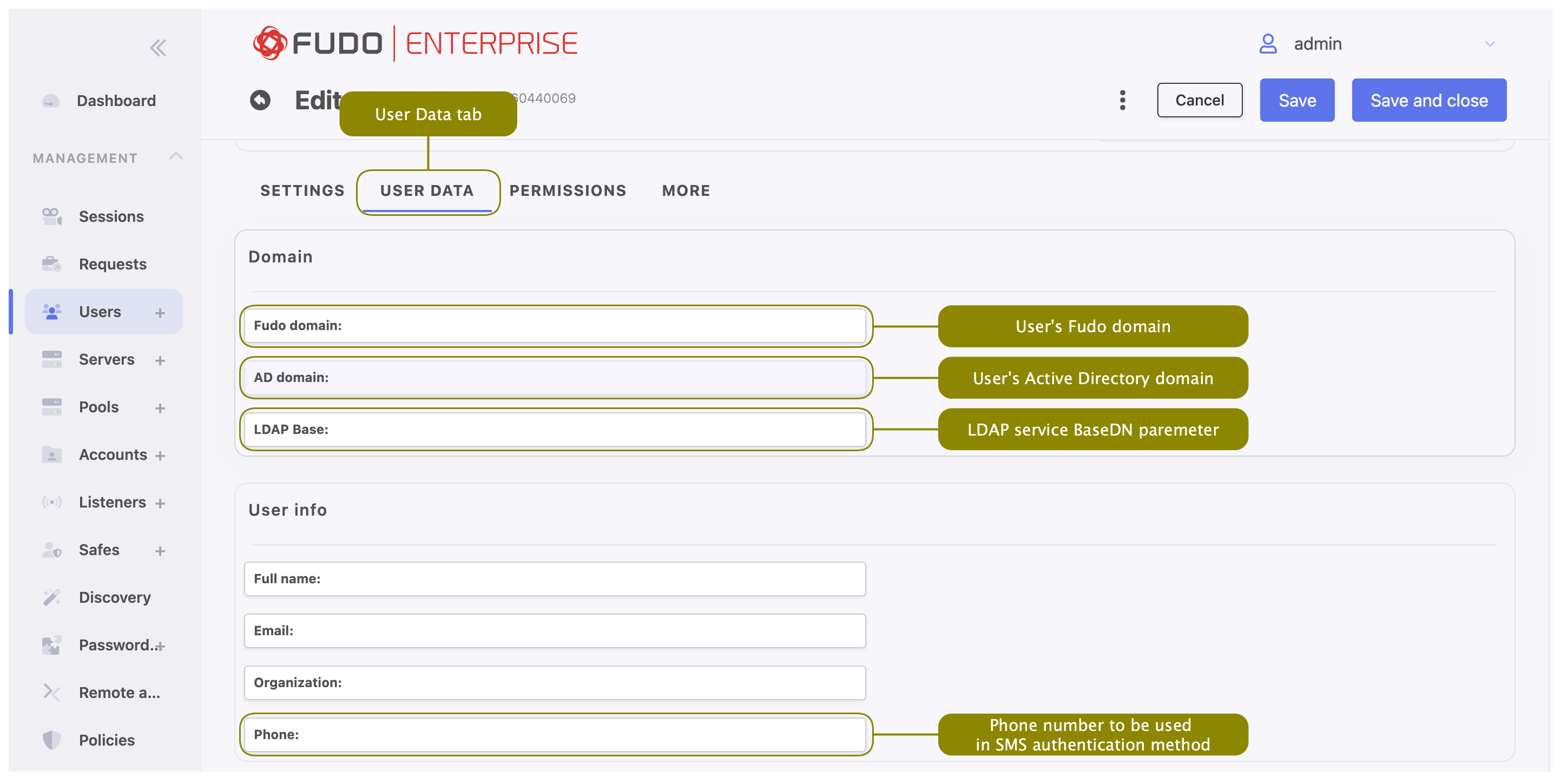
- In the User Data tab, in the Domain field, enter Fudo domain.
Note
- Fudo domain is used to authenticate the user against the Fudo Enterprise.
- With the Fudo domain specified, user will have to include it when logging into the administration panel and Access Gateway or when establishing monitored connections.
- Additionally to the Fudo domain it is possible to set up the Default domain in the System tab. If Default domain is specified, user can either include the Fudo domain in Username or skip it during login. Please refer to the Default domain section to learn more about the behavior of this option.
- Provide user’s Active Directory domain.
Note
While the Fudo domain is used to authenticate the user against the Fudo Enterprise, the AD domain is taken into account when authenticating the user in front of the server with which they establish a session. This option is related to the Fudo Domain settings in the user specification.
- Enter LDAP service BaseDN parameter.
Note
- LDAP base is necessary for authenticating the user using the Active Directory service.
- E.g. for
example.comdomain, the LDAP base parameter value should bedc=example,dc=com.
In the User info field enter:
- user’s full name,
- user’s email address,
- user’s organizational unit,
- user’s phone number.
- In the Permissions tab select button to choose users allowed to manage this User object and in case of Operator/Admin user role, assign management privileges to other objects, like servers, pools, accounts, safes, and listeners.
Note
Granting a user access to certain session requires assigning management priviliges to: server, account, user and safe objects that were used in the given connection.
- If created user is going to use the Application to Application Password Manager functionality, go to the More tab, and in the AAPM field, add IP address used by the User Portal (Access Gateway) and the AAPM to communicate with Fudo Enterprise.
- Optionally, to configure the Fudo Officer app, go to Fudo Officer field and click button. Download Fudo Officer application in App Store and scan showed QR code to finish mobile device binding. For more information please refer to the Fudo Officer 1.0 section.
Note
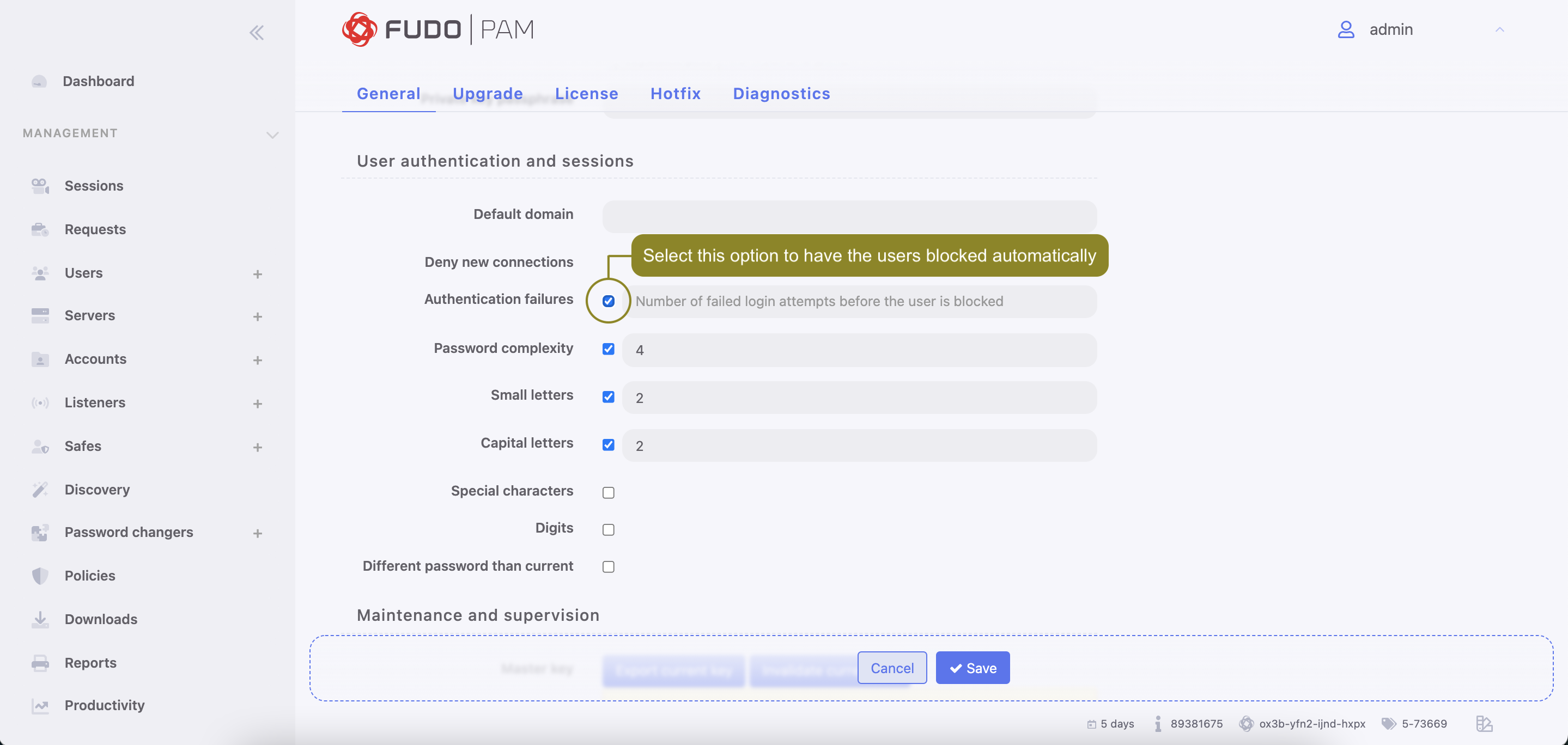
To add mobile device Call Home feature has to be enabled. Please navigate to > , and enable it on the General tab, under the Maintenance and supervision section.
- In the SNMP field, click Enabled to use SNMP, and provide authentication and encryption methods from the available drop-down lists.
Note
SNMP configuration is available only for user with the Service role.
- In the Authentication section, select the Authentication failures option to block the user automatically after exceeding the number of failed login attempts.
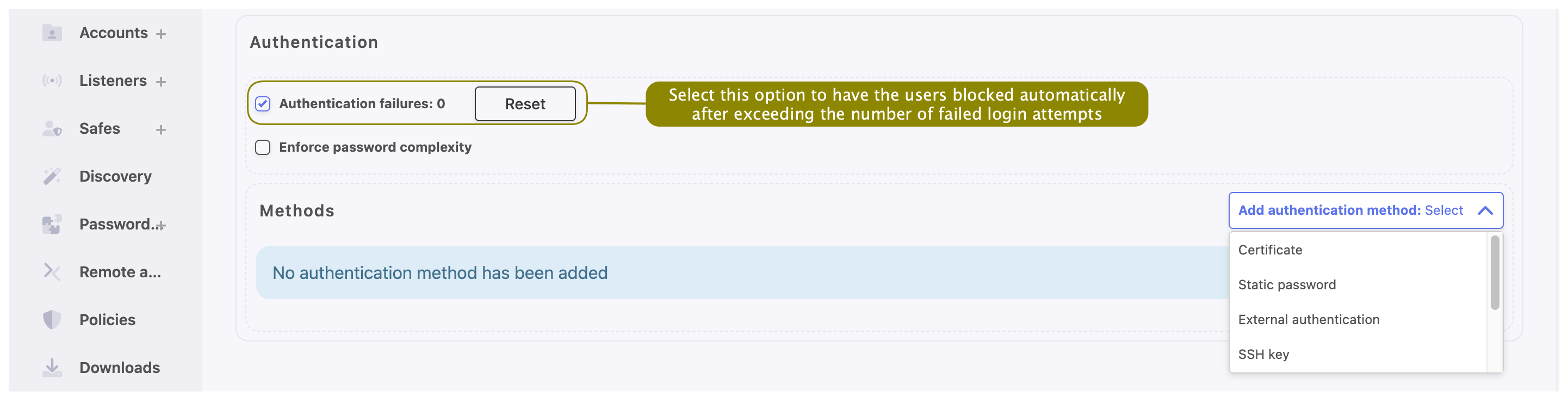
Note
The authentication failures counter is enabled only if the Authentication failures option is set in > in the User authentication and sessions section.
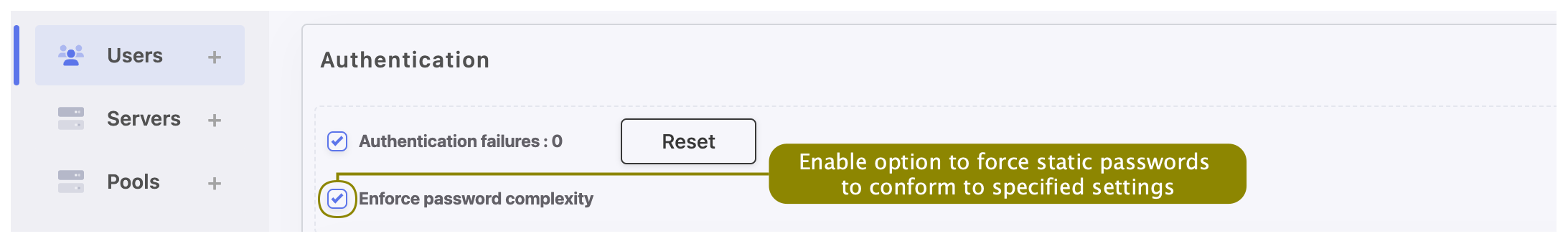
- Select the Enforce password complexity option to force passwords to conform to specified settings.
Note
Password complexity is defined in > in the Users authentication and sessions section.
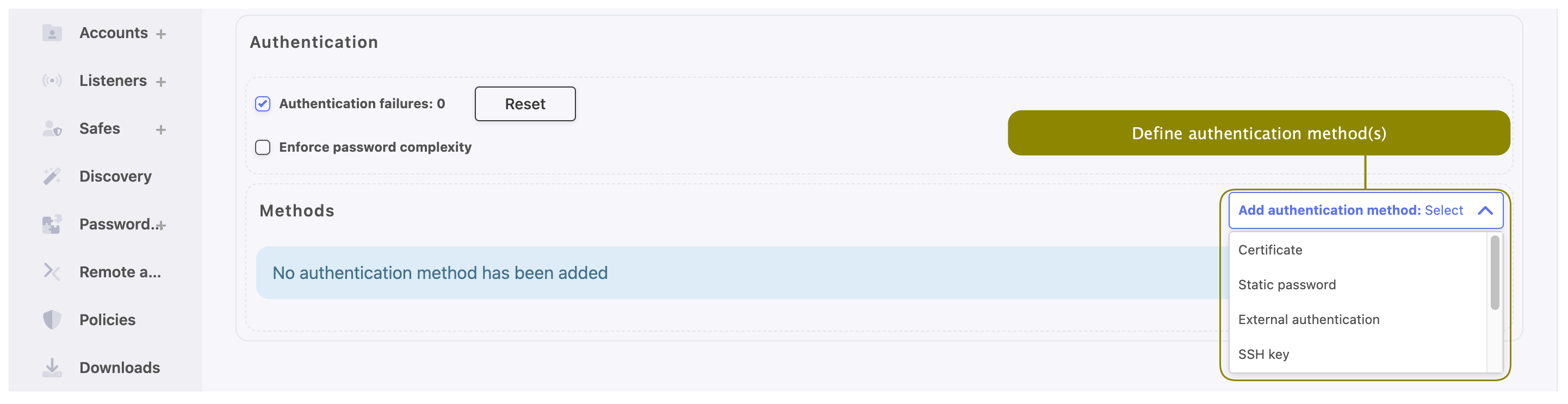
- Specify authentication methods.
Note
To enable configuring authentication methods, please save created user first.
- To add authentication method, select desired type from the Add authentication method drop-down list. Below you will find description of available authentication methods specification procedures.
Certificate
- Provide Subject that complies with the RFC 2253 or RFC 4514 requirements.
Note
Additionally, the CA certificate is required to be uploaded in the > tab. For more information about authentication with certificate, refer to the Certificate-based authentication scheme topic.
Static password
- Type password in the Password field.
- Select Required password change on next login to have the user change the password on next login attempt.
Note
If you select the Required password change on next login option, the user will not be able to access servers directly (bypassing the User Portal) using native protocols clients. The user will have to change the password using the User Access Gateway.
External authentication
- Select external authentication source from the Choose method drop-down list.
Note
Refer to Authentication topic for more information on external authentication sources.
SSH key
- Provide public SSH key used for verifying user’s identity in the Public key field.
SMS
- In the First factor field choose Static password or External authentication (AD or LDAP).
- Provide a phone number in the Phone input field.
Note
For more information about SMS authentication configuration, refer to the SMS authentication definition topic.
DUO
In the First factor field choose Static password or External authentication (AD or LDAP).
In the Second factor field:
- Provide DUO User.
- Provide DUO User Id.
Note
For more information about DUO authentication configuration, refer to the DUO authentication definition topic.
OATH
In the First factor field choose Static password or External authentication (AD or LDAP).
In the Second factor field:
- Provide Token type.
- Provide secret that will be used by Google Authenticator by typing it in the Secret field, by generating random secret by pressing Generate button, or by generating QRCode by pressing QRCode button.
- Specify Token length.
- Choose the timestamp value from the Timestamp drop-down list.
- Choose Initialized option if needed.
For more information refer to the Two-factor OATH authentication with Google Authenticator page.
API key
- Provide or generate API key.
- Copy generated API key to use it in other systems that require authentication with this Fudo user.
Note
The API Key cannot be retrieved after saving this authentication method.
- To define more authentication methods select new type from Add authentication method drop-down list.
Note
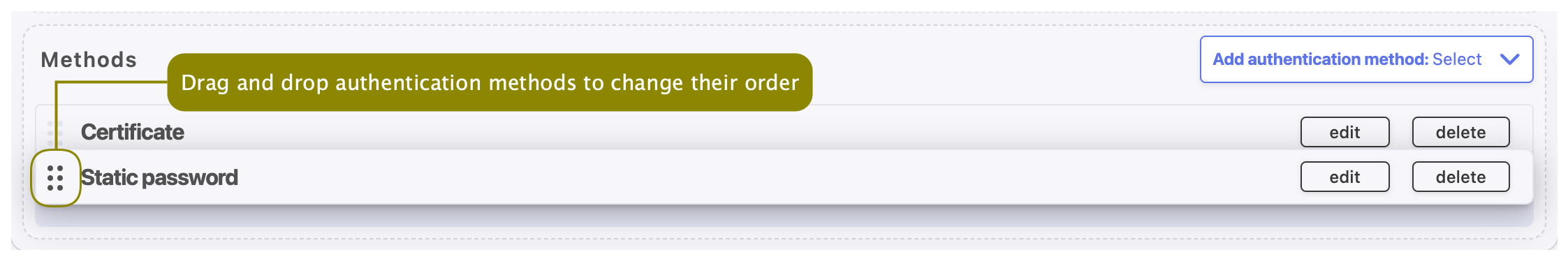
- When processing user authentication requests, Fudo Enterprise verifies login credentials against defined authentication methods in order in which those methods have been defined.
- After adding several authentication methods you have the possibility to change their order by using drag-and-drop functionality.
- Click or .
Related topics: