Using fudopv¶
Deprecated since version 5.4
Fudo Enterprise 5.4 is the last version supporting Application to Application Password Manager. The AAPM will be replaced by the functionality of APIv2 in the next release.
Execution parameters
When working with fudopv, the following command format is used:
fudopv [<options>] <command> [<parameters>]
The following table lists the available options for the fudopv command.
| Command/option/parameter | Description |
|---|---|
| Commands | |
getcert |
Fetch User Portal SSL certificate. |
getpass <type> <account_name> |
Fetch password to selected account. type:
|
Options for type fudo |
|
-s <address>, --server-address <address> |
Address of the server to which the account will connect. |
-p <port>, --port <port> |
Port of the server to which the account will connect. |
| General options | |
-c <path>, --cfg <path> |
Use configuration file from provided path. |
-h, --help |
Show options and parameters list. |
- Upload
fudopvscript to the server and change its access rights to allow execution.
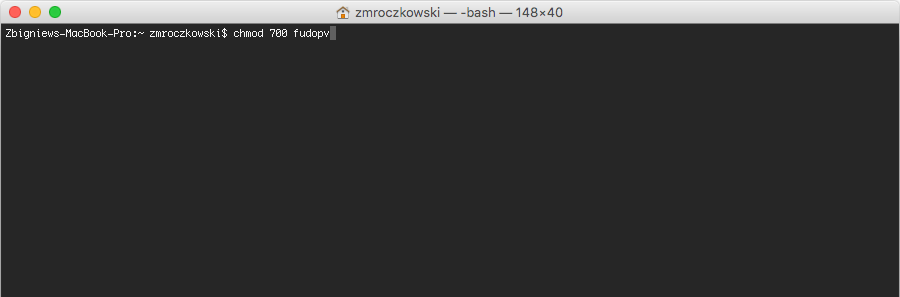
- Log in to the Fudo Enterprise administration panel.
- Create a user object with
userrole, static password authentication and server’s IP address defined in the API section.
Note
- Select > .
- Click .
- Enter user’s name.
- Define account’s validity period.
- Select User from the Role drop-down list.
- Assign safe and click the object to open its properties.
- Select the Reveal password option.
- In the Authentication section, select Password from the Add authentication method drop-down list.
- Type in the password in the Password field.
- If you want to limit the IP addresses allowed to access Fudo Enterprise over the API interface, go to the More tab, and in the AAPM field enter the IP address of the server, which will be requesting passwords using
fudopvscript. - Click .
- Run
fudopv getcertcommand to initiate the configuration.
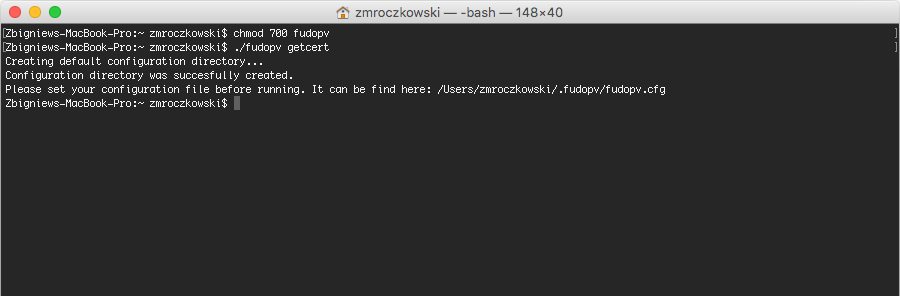
Note
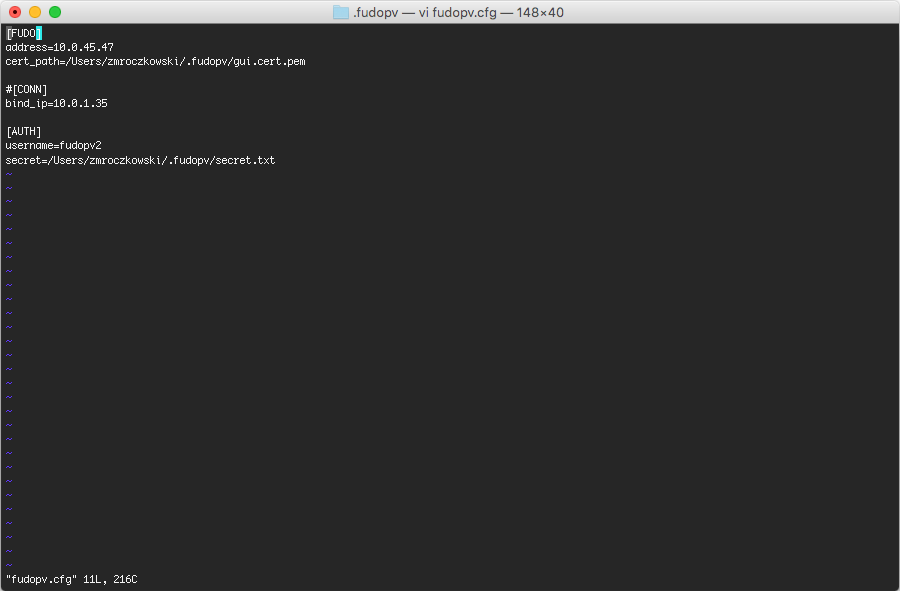
fudopv configuration files are stored in the .fudopv folder in user’s home folder.
- Open
fudopv.cfgfile in a text editor of your choice.
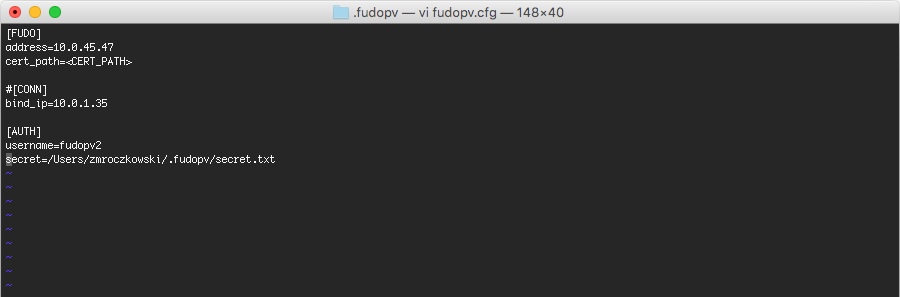
| Section | Description |
|---|---|
[FUDO] |
|
address |
User Portal’s IP address. |
cert_path |
Path to the User Portal’s SSL certificate files. |
[CONN] |
|
bind_ip |
IP address of the server, running the fudopv script. The IP address must be the same as the IP address defined in the API section in user configuration. This parameter is optional. |
[AUTH] |
|
username |
User login as defined in step 3. |
secret |
Path to the secret.txt file containing user’s static password. |
Note
- In the
[FUDO]section, in theaddressline, enter the User Portal IP address. - Leave the
cert_pathline as is, it will be updated automatically after successfully running thefudopv getcertcommand. - If you specified the IP address allowed to access Fudo Enterprise over API, in the
[CONN]section, uncomment thebind_ipline and provide the IP address of the server running thefudopvscript. - In the
[AUTH]section, in theusernameline, provide the login of the user object defined in step 3.
For example:
[FUDO]
address=10.0.0.8.61
cert_path=<CERT_PATH>
#[CONN]
bind_ip=10.0.0.8.11
[AUTH]
username=fudopv
secret=/Users/zmroczkowski/.fudopv/secret.txt
- Run
fudopv getcertcommand to fetch User Portal’s SSL certificate.
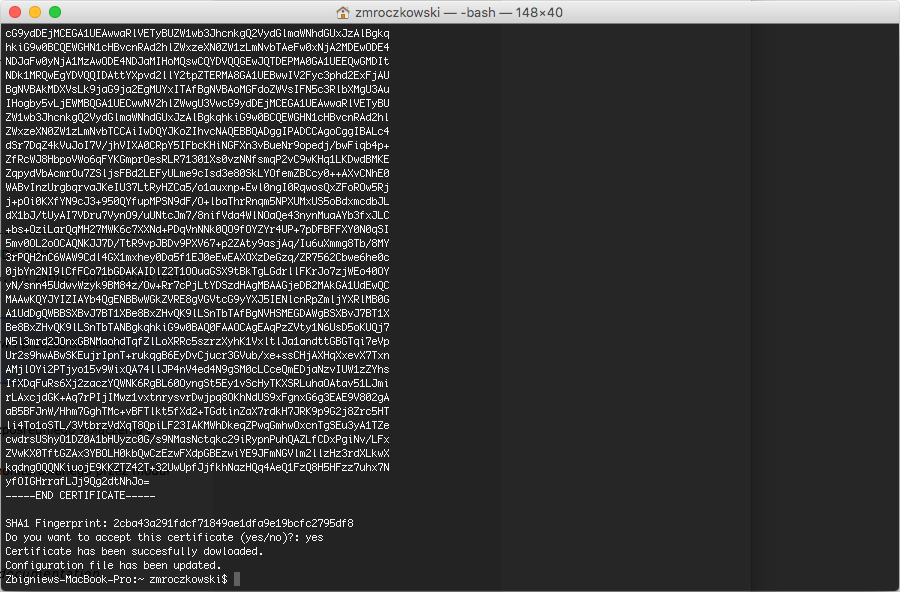
Note
After running the script successfully, the path to the certificate in the configuration file will be automatically updated.
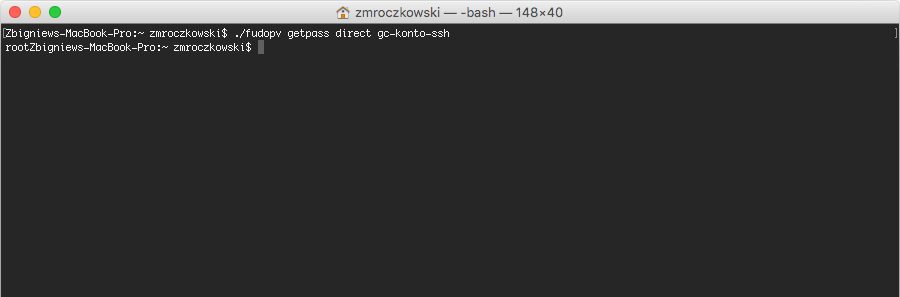
- Edit the
secret.txtfile and provide user’s static password. - Run command:
fudopv getpass direct <account_name>, to fetch password to connect directly to the server.
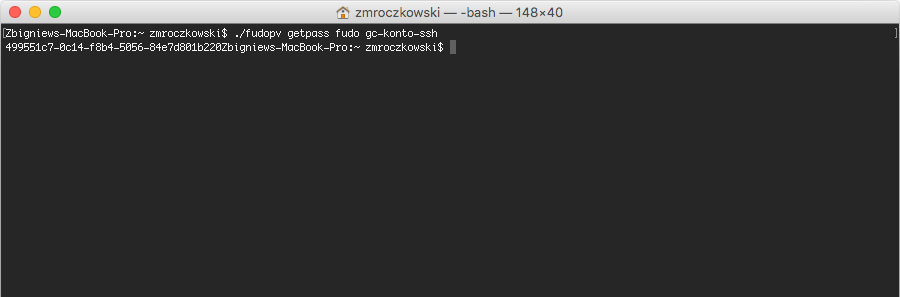
fudopv getpass fudo --server-address <address> --port <port> <account_name>, to fetch password to establish monitored connection with the target host.
Warning
Correct operation of the fudopv script requires disabling the Login reason prompt option in the safe’s properties.
Related topics: