Configuring Kerberos Constrained Delegation for MSSQL(TDS) Server¶
Note
Please note that this is a general guide, and specific details may vary depending on your Windows Server setup. Refer to the Windows Server documentation for precise configuration steps.
Kerberos Authentication Configuration on Windows Server¶
Configure DNS Entry:
- Open the Server Manager application.
- Click Tools button on the upper right corner of the window to expand the menu list and select DNS.
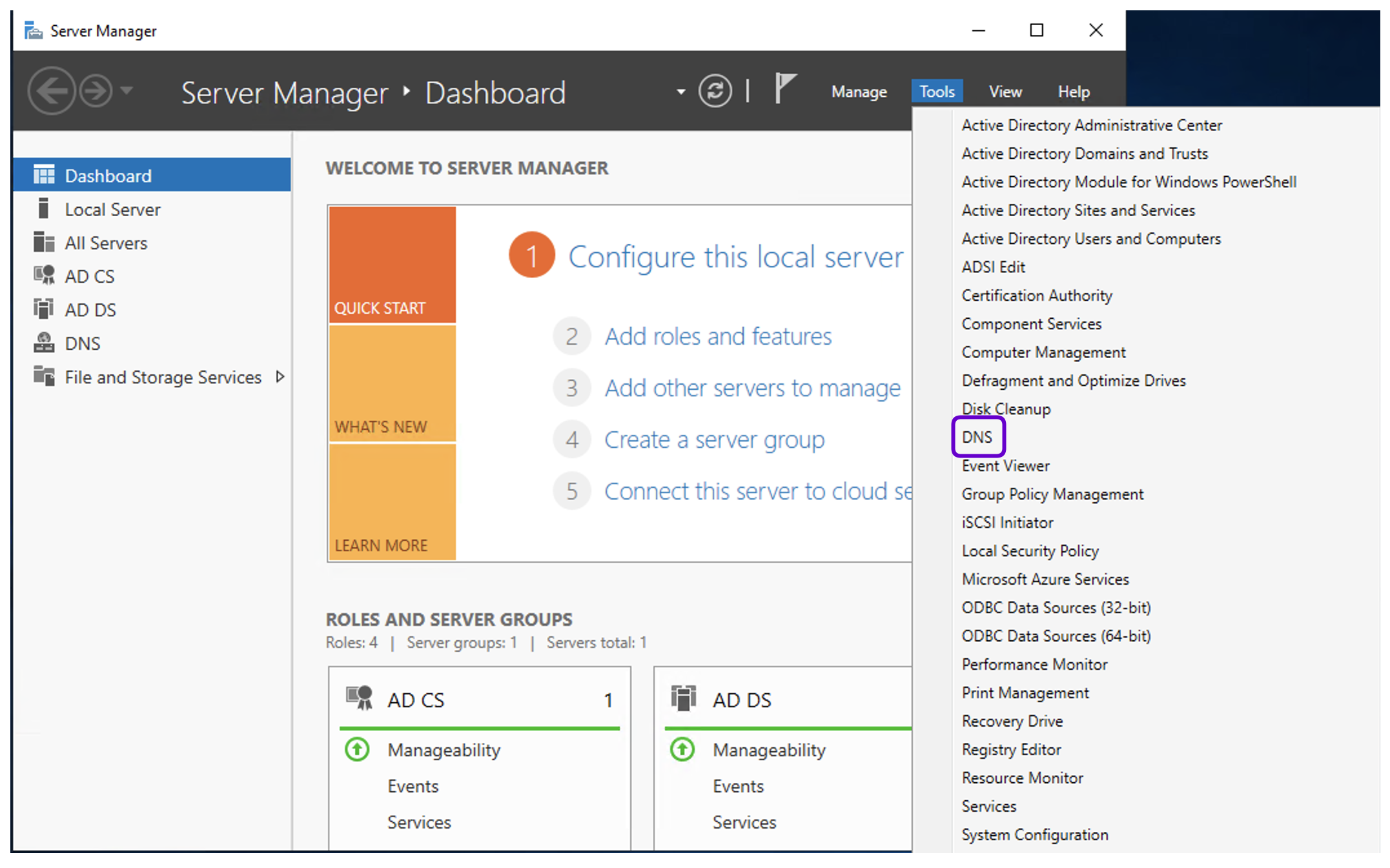
- Go to Forward Lookup Zones.
- Add an A record: right click on the selected domain name and click New Host (A or AAAAA).
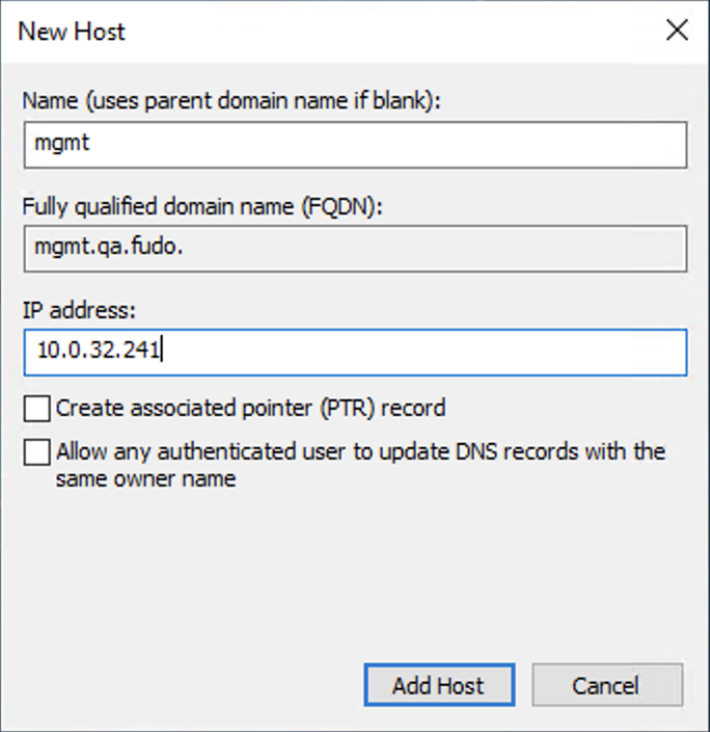
- Provide the Name and IP address of the Fudo Enterprise Admin Panel (e.g.,
mgmt.qa.fudo, 10.0.32.241).- Click Add Host.
Create Service User Account:
In this section we add the service user mssqluser, which will represent the MSSQL service in the domain.
- Log in to the server on which you want to setup the Kerberos using the administrator account.
- Open the Server Manager application.
- Click Tools button on the upper right corner of the window to expand the menu list and select Active Directory Users and Computers.
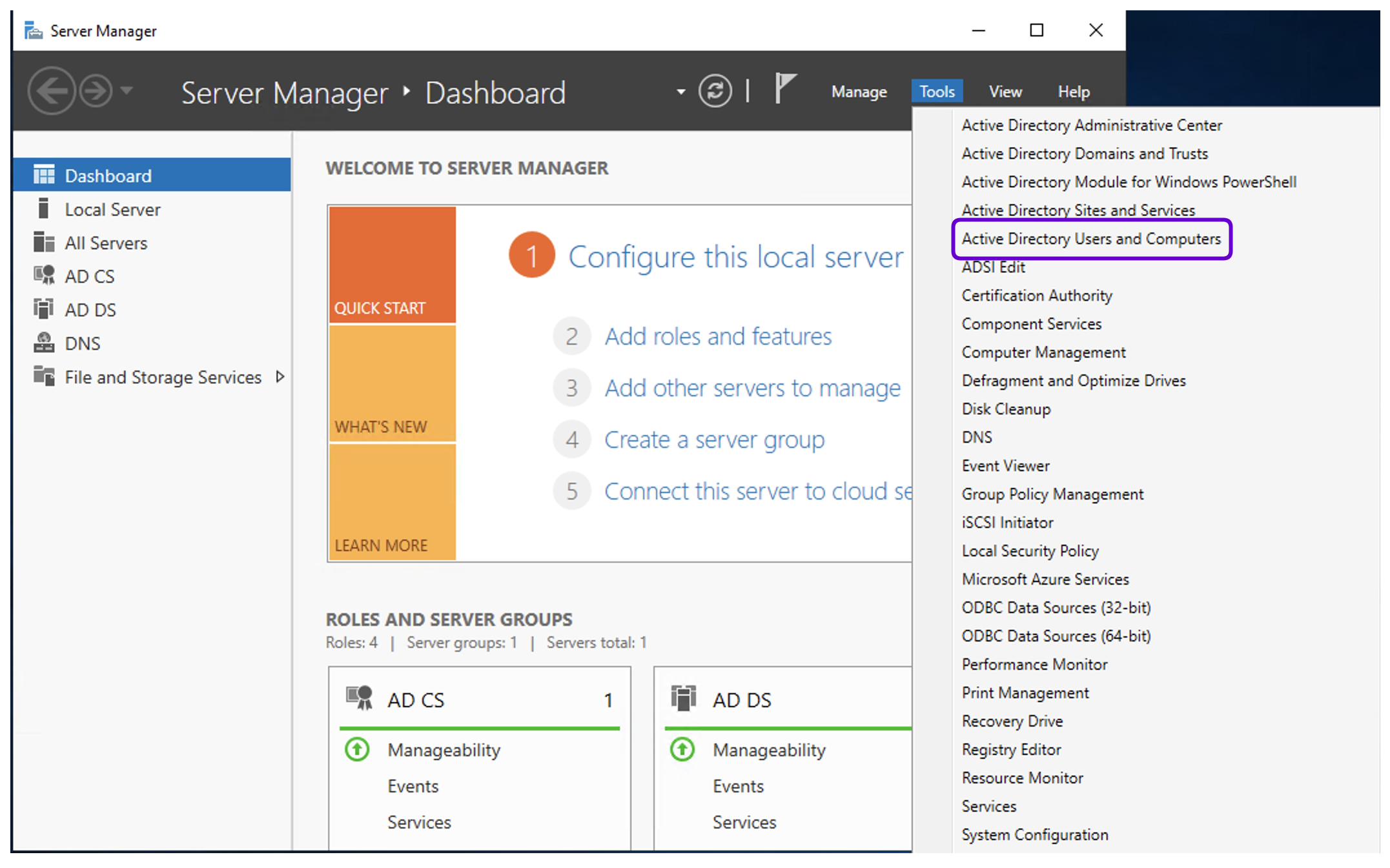
- In the Manager window, navigate to the domain name, or a specific user group, and right-click on the Users catalog.
- Select New > User.
- Create a user (e.g., User logon name:
mssqluser).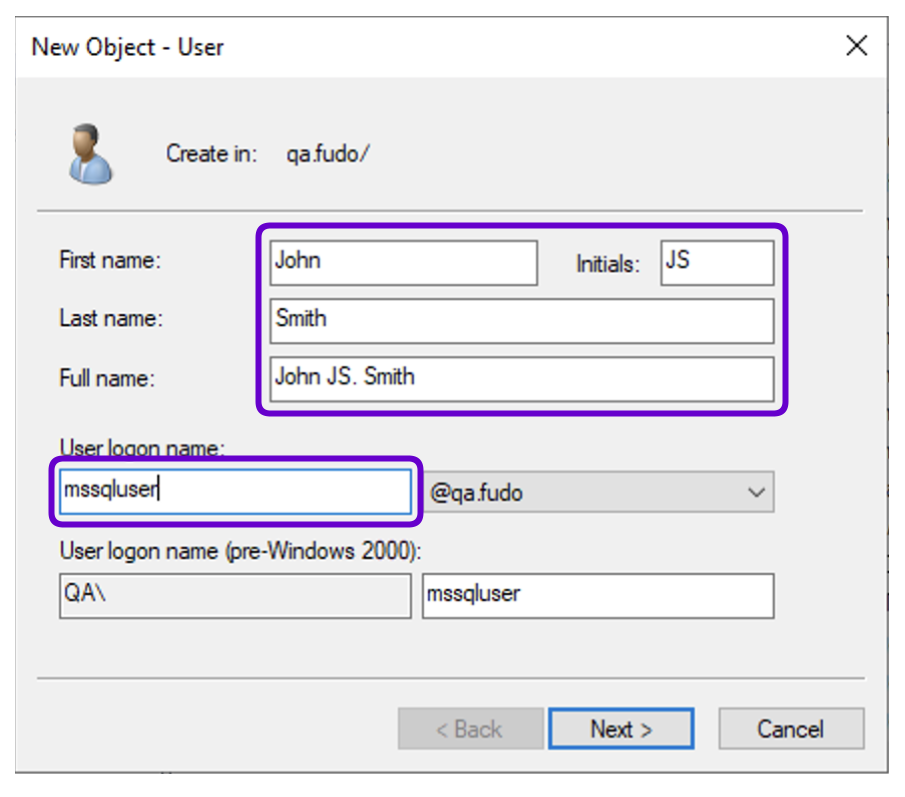
- Click Next.
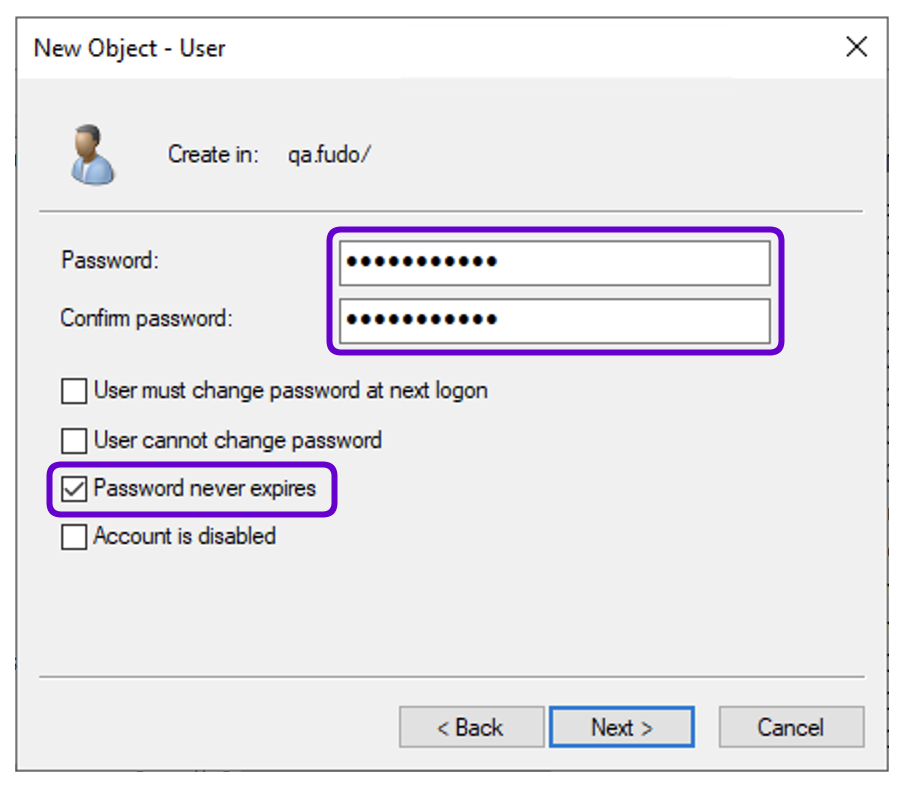
- Provide the password for created user (e.g.,
PaSSwOrD) and select Password never expires option.- Click Next and Finish.
Add an SPN (Service Principal Name) by running the following command in the PowerShell or CMD console:
setspn -S <service class>/<server name>.<domain>:<port>@<domain> <service account>Example:
setspn -S MSSQLSvc/WIN2019-DC1.qa.fudo:1433@QA.FUDO mssqluser
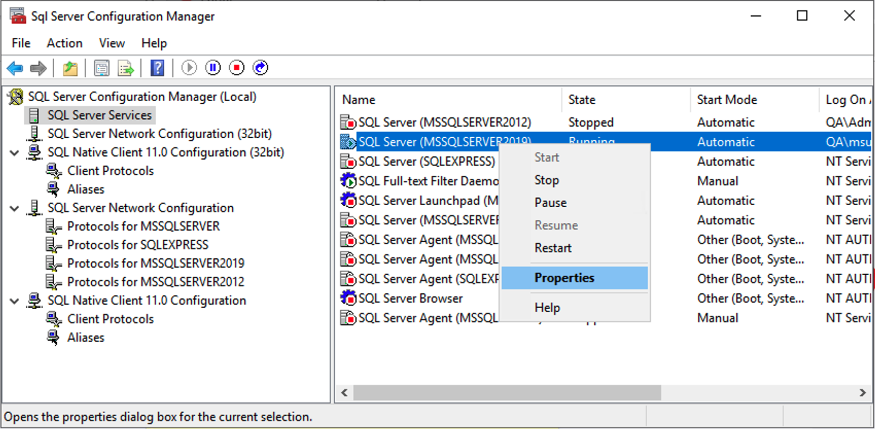
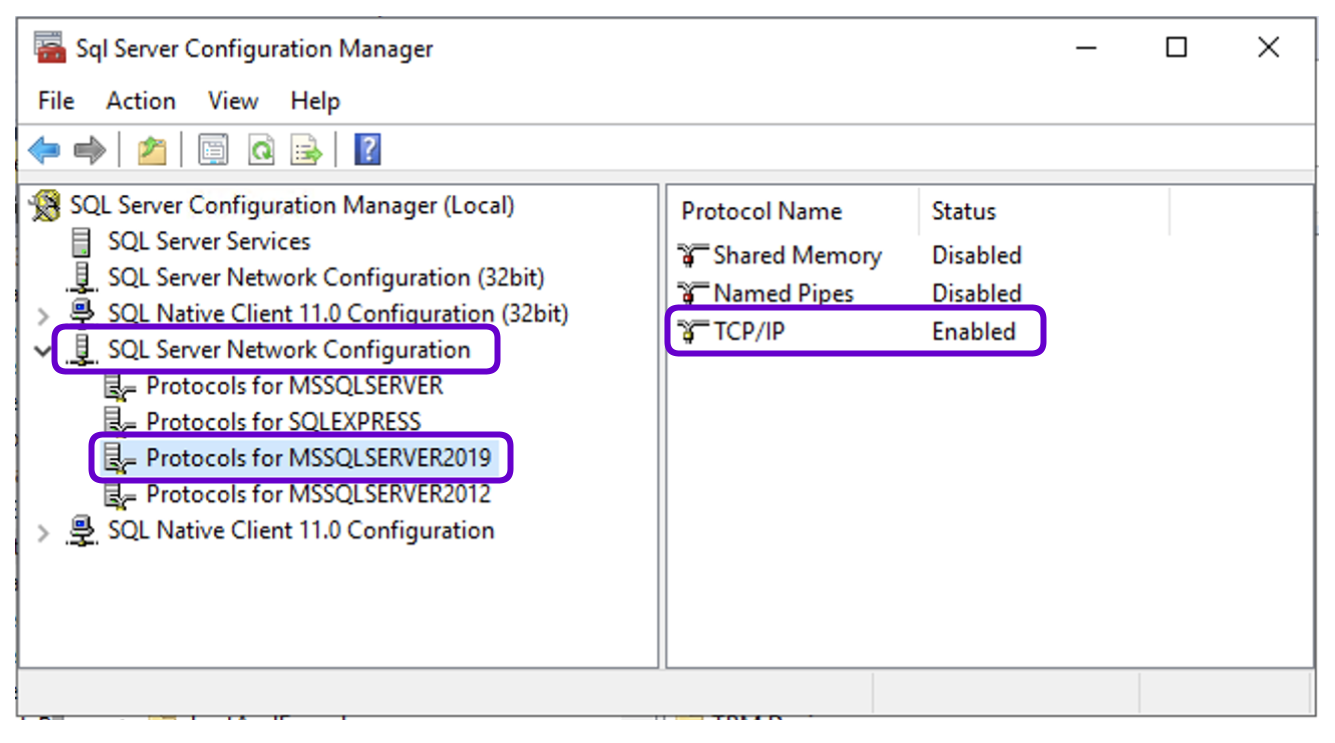
SQL Server Configuration Manager:
- Launch SQL Server Configuration Manager.
- Expand SQL Server Services, select the server, and open the Properties.
- In the Log On tab, enter the authentication credentials for the
mssqluseraccount.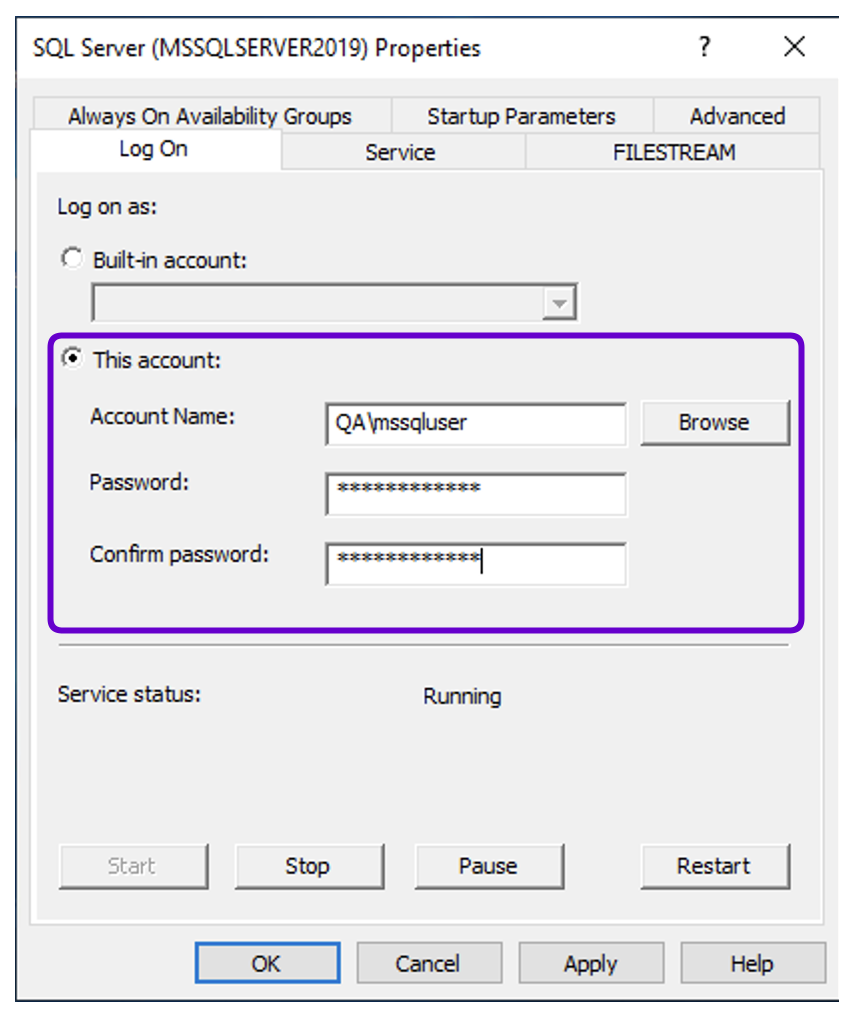
- Expand SQL Server Network Configuration, select the server, and ensure that the TCP/IP connection is enabled.
Create Service User representing MSSQL on Fudo:
In this section add the service user account mssqlfudo, which will represent the MSSQL service in Fudo Enterprise.
- Open the Server Manager application.
- Click Tools button on the upper right corner of the window to expand the menu list and select Active Directory Users and Computers.
- In the Manager window, navigate to the domain name, or a specific user group, and right-click on the Users catalog.
- Select New > User.
- Create a user who will use the Kerberos delegation to log in to MSSQL(TDS) server (e.g., User logon name:
mssqlfudo).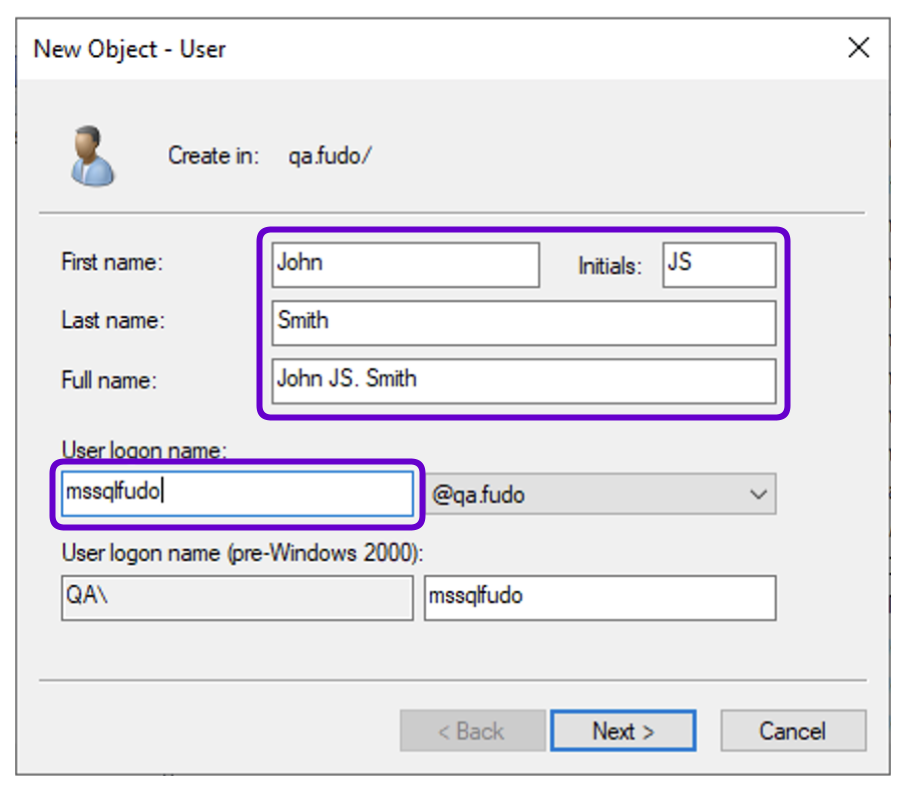
Click Next.
Provide the password for created user (e.g.,
PaSSwOrD) and select Password never expires option.Click Next and Finish.
Add an SPN (Service Principal Name) by running the following command in the PowerShell or CMD console:
setspn -S <service class>/<fudo admin panel name>:<port>@<domain> <service account>setspn -S MSSQLSvc/mgmt.qa.fudo:1433@QA.FUDO mssqlfudo
Kerberos Delegation
Note
- When the SPN is set for user
mssqlfudo, a new tab called Delegation appears in the user modification window.- If the Delegation tab is not visible, you may need to refresh the Active Directory Users and Computers management console.
Right-click on the
mssqlfudoaccount (created in the previous steps) in the Active Directory Users and Computers window, and select Properties.Go to the Delegation tab.
Select Trust this user for delegation to specified services only.
Choose Use Kerberos only.
Add the Services:
- Click the Add button.
- In the Select Users or Computers window, type
mssqluserand click Check Names to ensure accuracy.- Click OK to proceed.
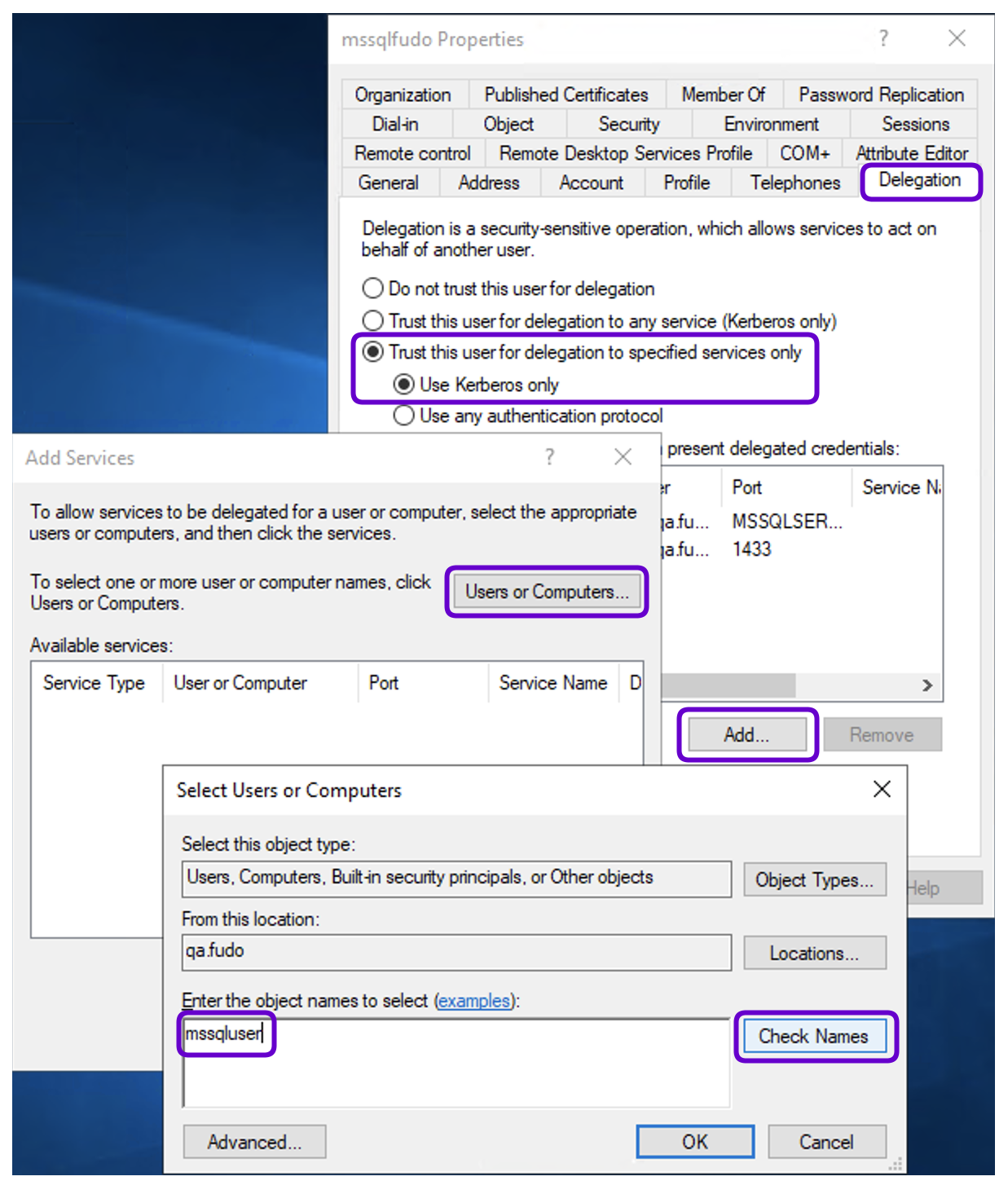
Select Services for Delegation:
- In the Add Services window, you will see a list of SPNs associated with the
mssqluseraccount.- Select all available services, or choose specific SPNs if needed.
- Click OK to confirm the selection.
Click Apply and then OK to save the settings.
If changes are not immediately visible, refresh the Active Directory Users and Computers console by pressing F5 or right-clicking on the Users container and selecting Refresh.
Generate Keytab:
Run the following command in the Powershell or CMD console:
ktpass -princ HTTP/hostname.yourdomain.local@yourdomain.local-mapuser netbios_domain_name\username -pass password -ptype KRB5_NT_PRINCIPAL-out hostname.yourdomain.local.keytab
- Example for this use case:
ktpass -princ MSSQLSvc/mgmt.qa.fudo:1433@QA.FUDO -mapuser QA\mssqlfudo-pass PaSSwOrD -pType KRB5_NT_PRINCIPAL -out mssqlfudo.keytabCopy the generated keytab file to the workstation where you will be configuring Fudo.
Note
It is an alternative authentication method to using a password. The password must match the one specified when creating the user. If the user’s password is changed, their keytab will be invalidated.
Setup Fudo Enterprise¶
Configure DNS:
- Go to > .
- Switch to the Name & DNS tab.
Configure DNS server to point to a DNS server in the yourdomain.local domain (in this example we will use a domain controller IP address):
- Click to define new DNS server.
- Enter DNS server IP address (e.g.,
10.0.242.100).- Click .
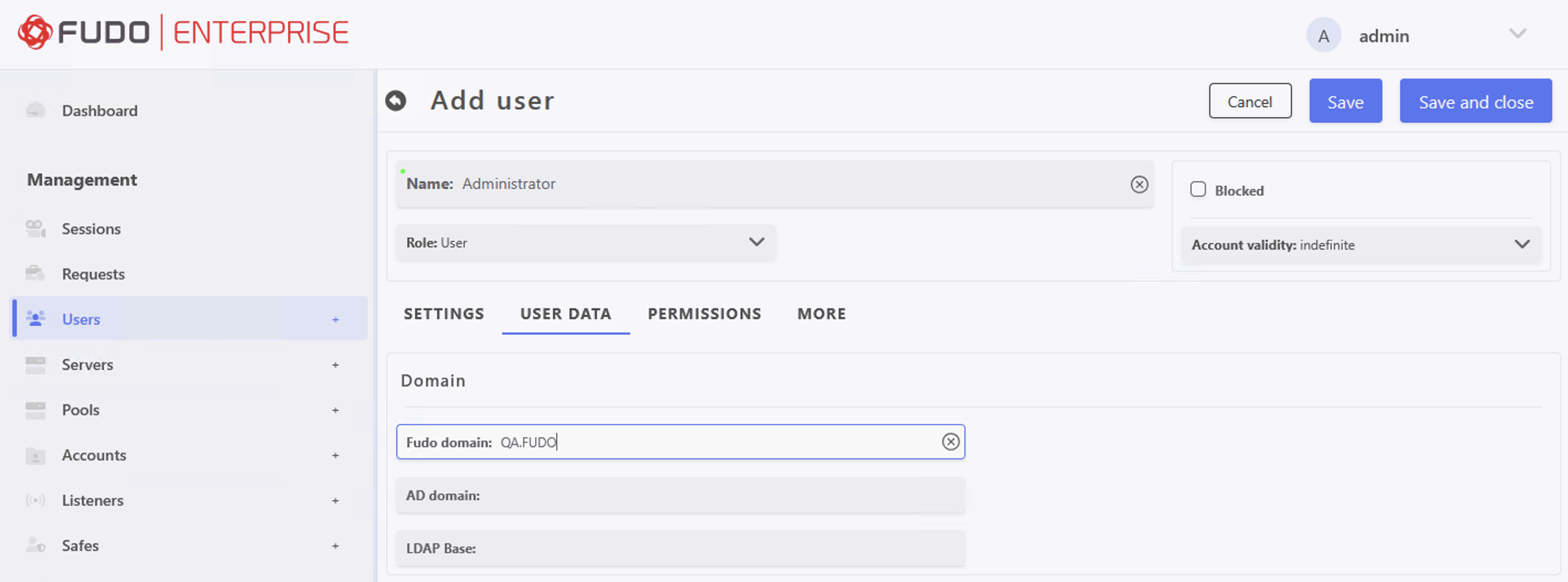
Create User in Fudo:
- Select > and then click .
- Enter the user name that matches created in previous steps user account in Active Directory (e.g.,
Administrator).- Select the
userrole.- In the Settings tab, under the Safes section, select main to grant access rights to the Admin Panel.
- Click .
- Go to the User Data tab, and fill in the Fudo domain (e.g.,
QA.FUDO).Note
The Fudo domain should match the domain name specified in the Kerberos ticket.
- If necessary, please fill in the remaining parameters as needed for your specific configuration. For more details, please refer to the Creating a user section.
- Click .
Configure MSSQL(TDS) Server:
- Select > and then click .
- Enter server’s unique name (e.g.,
tds).- In the Settings section on the list of available protocols select
MSSQL(TDS).- In the Destination section select
Hostand enter server’s host name (in our example,win2019-dc1.qa.fudo).- Enter port:
1433.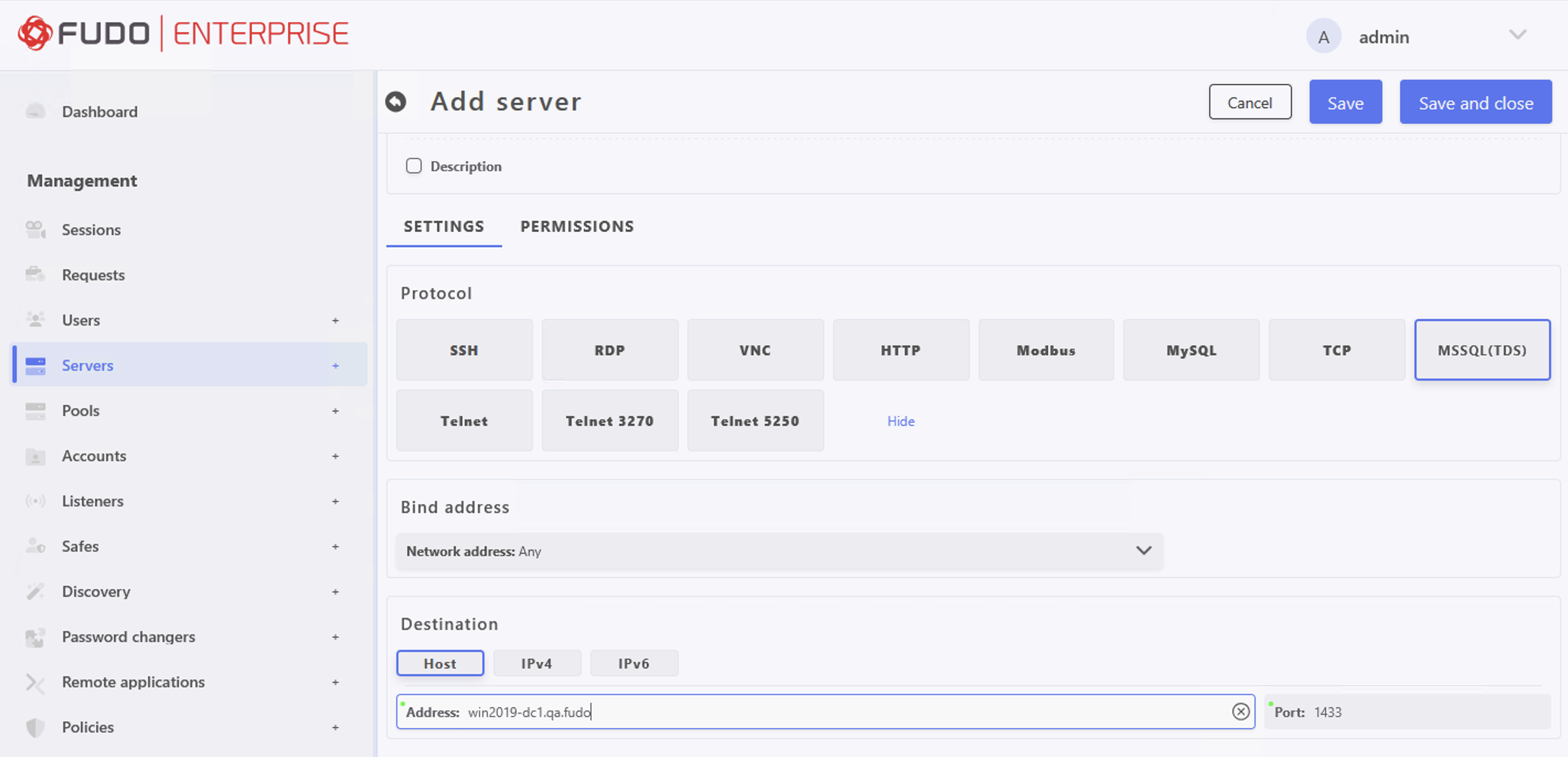
- Click .
Configure Account:
- Select > and then click .
- Define object’s name (e.g.,
tds:forward).
- In the Type section select
- In the Target section click , and from the drop down list select server created in previous step (e.g.,
tds) to assign created account to this server.- In the Replace secret with section select .
- Click .
Note
The forward account type is recommended in this scenario because S4U2Proxy delegation requires using the existing user ticket to authenticate against the TDS server. Therefore, the username of the user who logged in to Fudo Enterprise is always used, and the credentials entered for the account will not be utilized.
Configure Listener
- Select > and then click .
- Enter listener’s unique name (e.g.,
tds-listener).
- Go to SETTINGS tab and press the button in the Protocol field.
- Select Enable constrained delegation option.
- In the Service principal name field, enter the following:
MSSQLSvc/mgmt.qa.fudo:1433@QA.FUDO.- Upload Keytab file.
- In the Connection mode section, select .
Note
It is possible to use
bastionmode, but it will not be possible to use bastion login strings.
- Set the local address (e.g.,
Any), and port1433.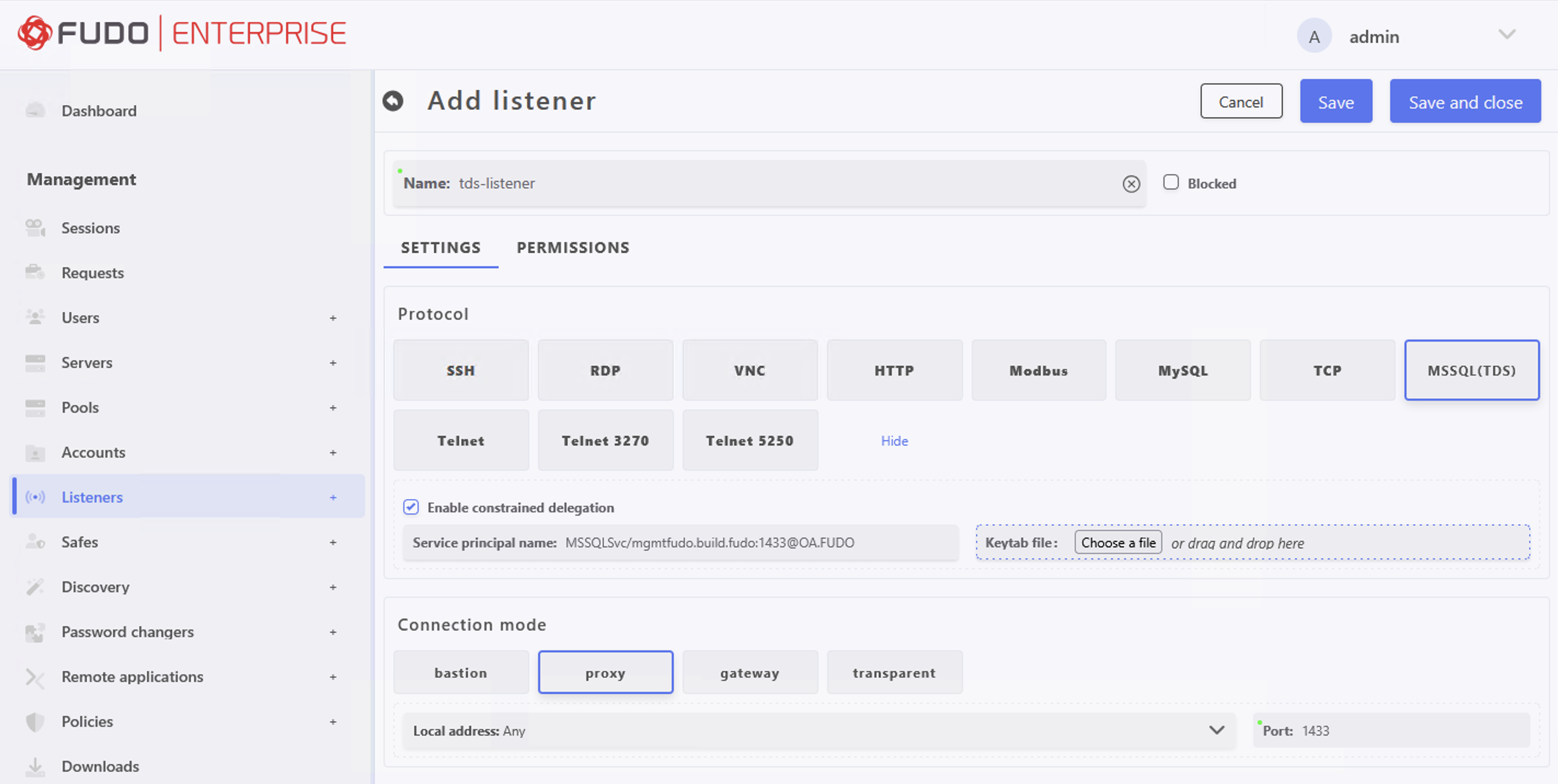
- Click .
Configure Safe:
Select > and then click .
Enter safe’s unique name (e.g.,
tds-safe).Click to save the object and proceed with further configuration.
Go to the Users tab to assign users allowed to access accounts assigned to this safe.
- Click .
- Mark the checkbox in front of the users’ names to enable their server access through the monitored safe (e.g.,
user1).- Click to close the modal window.
Select Accounts tab to add accounts accessible through this safe.
- Click .
- Mark the checkbox in front of the accounts’ names to add it (e.g.,
tds:forward).- Click to close the modal window.
- Select added account and click to assign listener (e.g.,
tds-listener).- Click to close the modal window.
Click to save the safe configuration.
Establish a Connection¶
Note
Logging in using typical SQL Server Authentication is also possible when using a listener with constrained delegation enabled.
Related topics: