External authentication server definition¶
To add an external Active Directory, LDAP, Cerb, or Radius authentication server, proceed as follows.
- Select > .
- Choose External authentication tab.
- Click .
- Provide a name for this specific configuration.
- Select the bind address - IP address used for sending requests to given host.
Note
In case of cluster configuration, select a labeled IP address from the Bind address drop-down list and make sure that other nodes have IP addresses assigned to this label. For more information refer to the Labeled IP addresses topic.
- In the General section, elect authentication service type:
Active Directory, LDAP, CERB,orRadius.
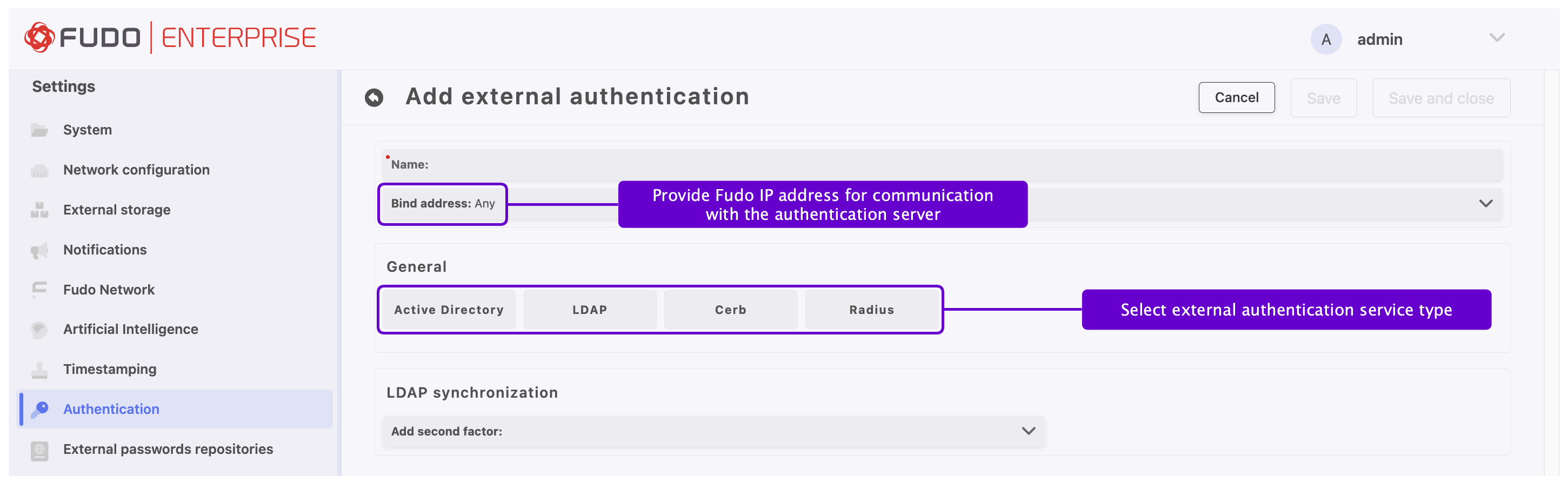
- Provide configuration parameters depending on selected external authentication system type.
- Click .
Field Descriptions and Configuration Based on Chosen Method
| Parameter | Description |
|---|---|
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Active Directory domain | Domain which will be used for authenticating users in Active Directory. |
| TLS enabled | This option is required to be checked for the domain users who change their passwords in the Access Gateway. |
| Server certificate / CA Certificate | Active Directory server certificate or CA certificate. Available when TLS enabled option is activated. |
| Privileged user login | The privileged account’s login name to modify a user password on the Active Directory server. |
| Secret | Secret used to establish server connection to modify a user password on the Active Directory server. |
| Add second factor | Additional verification step with authentication methods OATH, SMS or DUO. |
Note
- The Active Directory external authentication method uses the Kerberos protocol as the first step.
- This functionality is enabled by default.
- Please refer to Kerberos authentication settings section to learn how to disable it.
- If Active Directory authentication is successfully completed using Kerberos, the configured certificate will not be applied, as it is only utilized when a fallback to LDAP is required.
| Parameter | Description |
|---|---|
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Bind DN | Template containing a path which will be used to create queries to LDAP server. |
| TLS enabled | This option is required to be checked for the domain users who change their passwords in the Access Gateway. |
| Server certificate / CA Certificate | LDAP server certificate or CA certificate. Available when TLS enabled option is activated. |
| Add second factor | Additional verification step with authentication methods OATH, SMS or DUO. |
| Parameter | Description |
|---|---|
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Service (NAS ID) | CERB service used for authenticating Fudo Enterprise users. |
| Secret | Secret used to establish server connection. |
| Add second factor | Additional verification step with authentication methods OATH, SMS or DUO. |
Note
The AD domain field from the user configuration is included in the initial Access-Request packet used to authenticate the user against the RADIUS/Cerb server.
- If the AD domain is populated:
- For RADIUS, the AD domain value is appended to the username in the
User-Namefield, formatted as:{name}@{ad_domain}.- For Cerb, the
MS-CHAP-Domainfield is set to the value from the AD domain, and theUser-Namefield contains only{name}.- If the AD domain is not populated, the
User-Namefield in theAccess-Requestpacket for both methods contains only the username:{name}.
| Parameter | Description |
|---|---|
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| NAS ID | RADIUS server NAS-Identifier parameter. |
| Secret | Secret used to establish server connection. |
| Add second factor | Additional verification step with authentication methods OATH, SMS or DUO. |
Note
- Please note that when configuring Radius authentication within Fudo Enterprise, only the Password Authentication Protocol (PAP) is supported.
- Make sure to read the note for the Cerb method as well.
Warning
When additional authentication method (OATH, SMS or DUO) is selected as a Second factor for synchronization with External authentication server (AD / LDAP / CERB / RADIUS), it won’t be enough to just select one of the External authentication server source within the User definition. The additionally selected authentication method should be configured within the User definition as a primary authentication method. Then users’ authentication methods will be automatically synchronized according to External authentication server settings.
Related topics: