OpenID Connect authentication definition¶
This authentication method is configured globally and is not tied to any particular user. Thus even if a user has no authentication methods configured, they can authenticate using OpenID Connect in Access Gateway and Admin Panel.
Follow the steps to configure the OpenID Connect authentication method:
- Select > .
- Choose OpenID Connect tab.
- Click .
- Check the Enabled option to globally enable OpenID Connect authentication.
- Provide Name (
Azure,Oktaor any other Identity Provider). - Provide Bind address.
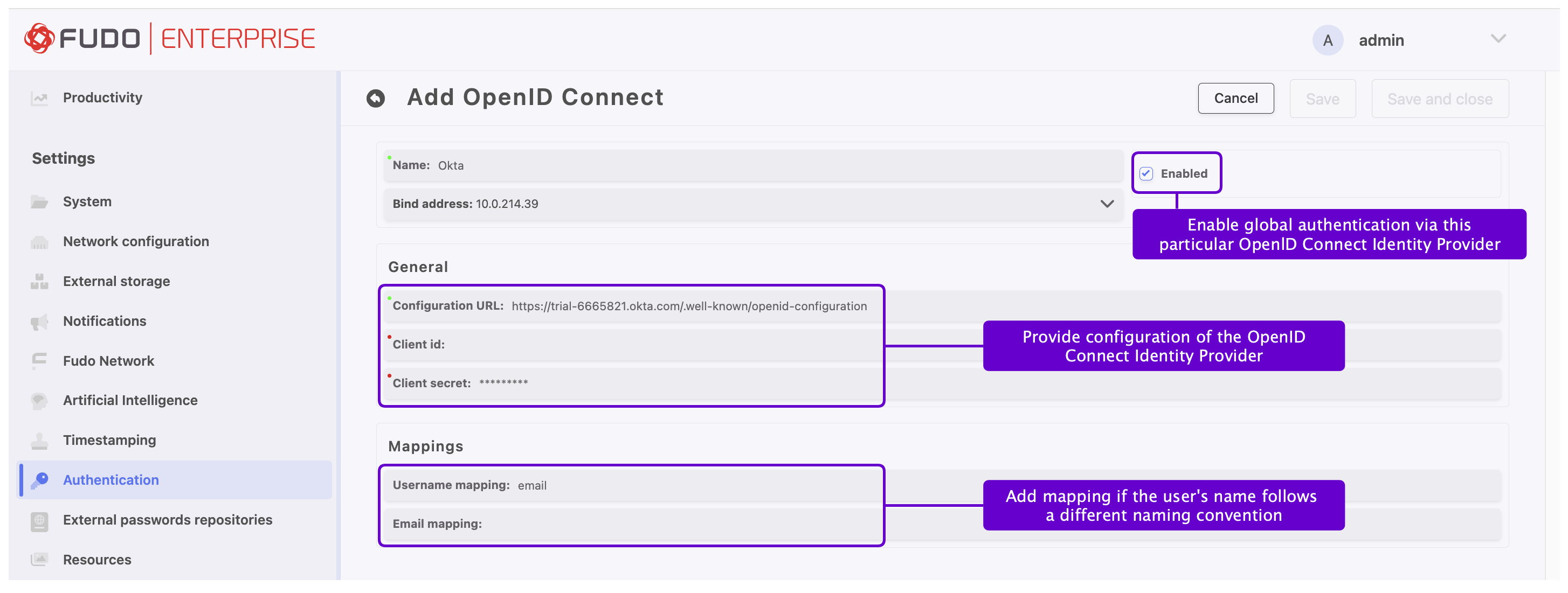
- In the General section, input Configuration URL.
Note
This URL is specific for every Identity Provider and allows identifying one for correct configuration. Example of Configuration URL for Google: https://accounts.google.com/.well-known/openid-configuration.
- Provide Client ID, and Client secret. Those values are available after registering with the selected provider.
Note
Please refer to the section OpenID Connect authentication definition with Microsoft Entra (Azure) for a use case example on configuring OpenID authentication using the Microsoft Entra.
- In the Mappings field, add Username mapping and Email mapping if necessary. These fields are useful when the user’s name follows a different naming convention.
Note
To ensure proper authentication via Okta external provider, specific mapping configurations are required based on the format of the user’s name and the presence of the email address in the User configuration.
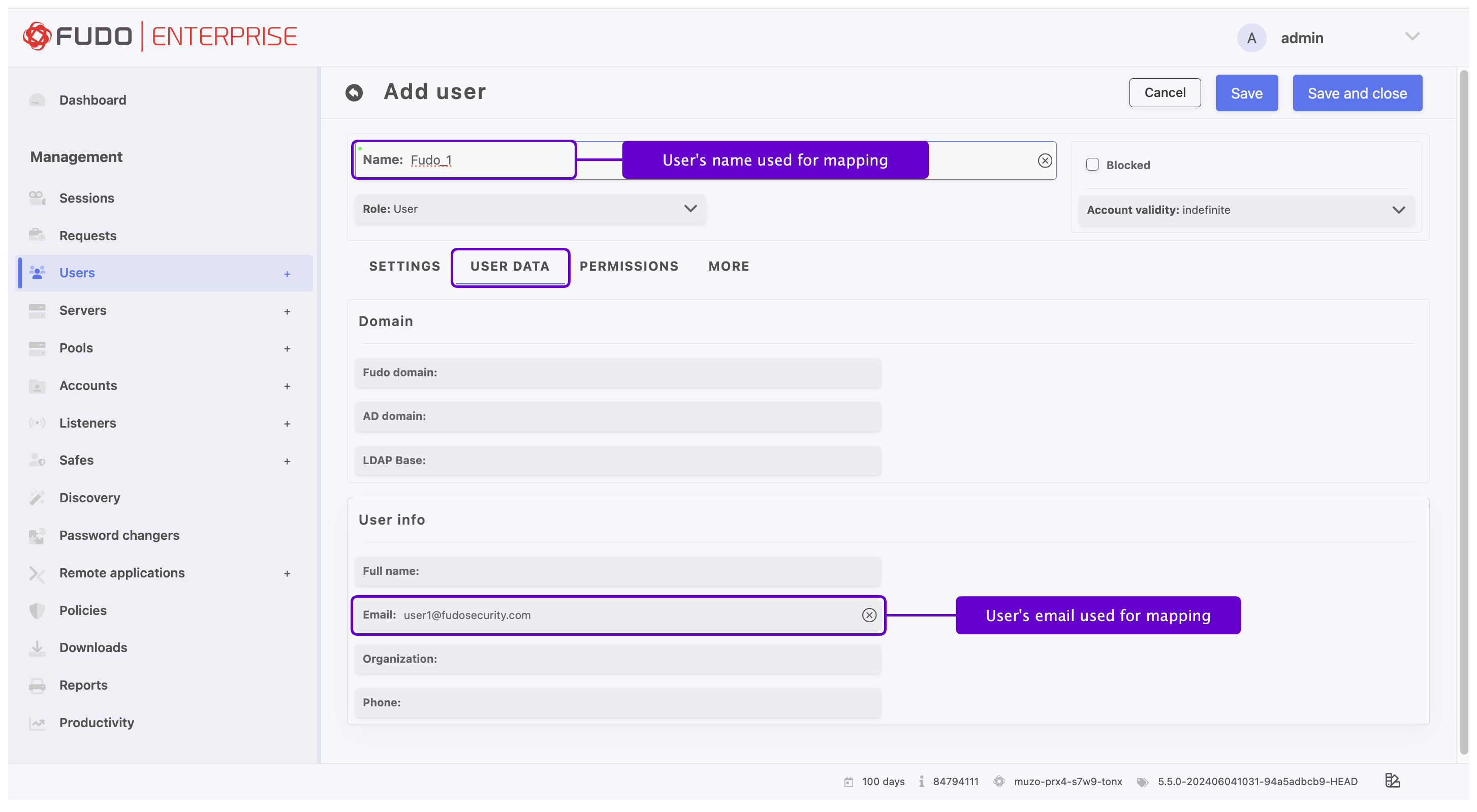
Username Contains Email Address:
Scenario: If the Name field in the User configuration includes an email address (e.g.,
user1@fudosecurity.com) and the Email field in the User Data tab is empty.Configuration: Set the Username mapping to
email.This ensures that the email address within the username is correctly recognized and used for authentication purposes.Username with Text and Email Field Populated:
Scenario: If the Name field in the User configuration contains any text (e.g.,
Fudo_1,user1) and the Email field in the User Data tab contains the actual email address (e.g.,user1@fudosecurity.com).Configuration: Set the Email mapping to
email. This configuration ensures that the email address provided in the Email field is used for authentication, even if the username is a non-email string.
- Click .
Note
The algorithm to determine the user’s identity is following:
- The user is initially identified using the
subclaim from the OpenID Connect (OIDC) provider.- If the user is not identified using the
subclaim from the OIDC provider, the next step involves checking the autolink setting for the OIDC provider. If this setting is false, the process concludes without finding the user. However, if the autolink setting is true, the search process continues.- If Username mapping is defined, a search for a corresponding claim in the data is conducted. Once the claim is located in the JSON data, the system then looks for the user with that name.
- If Username mapping is not defined, the claim is not found in the data or the user is not found by name, the next step is to verify if Email mapping is defined. If it is defined and exists in JSON data, the process then tries to identify the user based on this email.
- When neither Username mapping nor Email mapping is defined, the system will seek to identify the user by their name or email. This is done by searching for the
upnorunique_nameclaims within the data, in this specified order.- When the
email_verifiedfield to be included in the data and set totrue.- The last step checks if the found user has a
subclaim stored already, but different from the one received from the OIDC provider. If they don’t match, it fails.- The received user
subclaim is stored in the database for future use.
- Log in using the defined authentication method:
Related topics: