Policies¶
Policies are patterns definitions facilitating proactive session monitoring. In case a defined pattern is detected, Fudo Enterprise can automatically take respective actions and notify the administrator about the current situation.
Fudo Enterprise divides policy definition by its basis: AI module or Regular Expression:
- when the
AI moduleoption is chosen as a basis of the policy, Fudo Enterprise reacts on reaching the specified Threat Probability Threshold, - when the
regular expressionoption is chosen for the policy’s base, the system analyses the defined expression’s input or output.
Both types of policies react by taking the following actions:
- sending e-mail message,
- sending SNMP TRAP notification,
- pausing connection,
- terminating connection,
- blocking the user.
AI module-based policy¶
In order to configure an AI module-based policy, proceed as the following states:
- Select > .
- Click .
- Provide the Name for the policy.
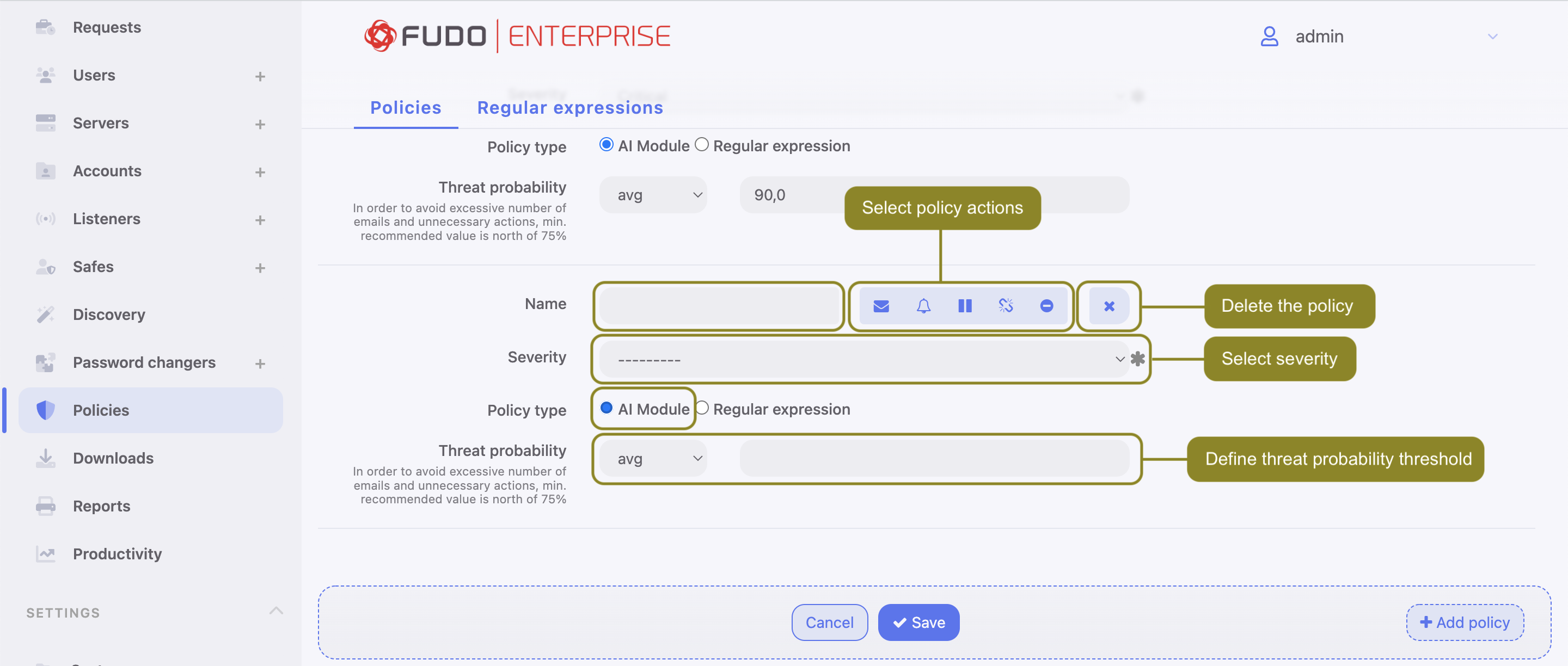
Select the actions that will be performed when the policy is breached:
- - send email notification to system administrator.
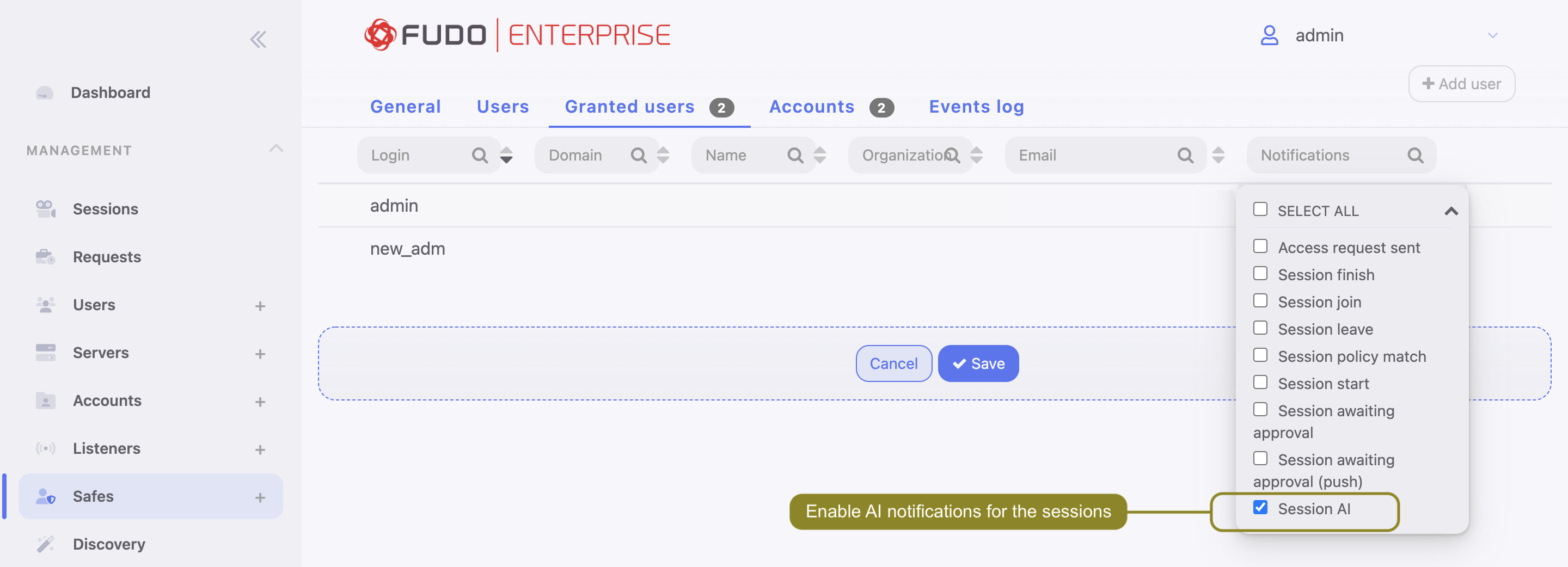
Note
Sending email notifications requires configuring and enabling notification service as well as Session AI notification enabled in safe configuration.
- - send SNMP TRAP notification to the receiver.
Note
Sending SNMP TRAP notifications requires configuring the SNMPv3 TRAP in the System tab. Check the SNMPv3 TRAP page for more information.
- - pause connection.
- - terminate connection.
- - block user.
Warning
If SNMP TRAP service is not configured, all notifications on policy violation will be discarded but other options related to the session management will work.
- Select the Severity. Severity parameter value is included in the email notification message and in the Events log with the
FSW0284code. - Check the
AI modulein the Policy type field. - Select
min,avg(default) ormaxoption for the Threat Probability Threshold field and provide the value.
Note
Values for the Threat Probability metrics are calculated by the AI models for each session segment. The segment evaluations are averaged per model (e.g. Mouse Biometric, Keyboard Biometric) creating a model Threat Probability, thus the AI model delivers one Threat Probability per model for the whole session. These values are used in the policy and the policy actions can be applied to the minimum, average or maximum value of model Threat Probabilities.
In practice, if an administrator wants to decrease sensitivity of the policy so that it reacts to breaching a given threshold by all the models, the Threat Probability Threshold should be set to minimum. If the situation requires the policy to be more sensitive and react to the threshold breaching by at least one model, then the Threat Probability Threshold should be set to maximum.
Default value for the Threat Probability Threshold is average.
In order to avoid an excessive number of emails and unnecessary actions, min. recommended value is above 75%.
- Click .
AI module-based policy examples
Example 1. Sending SNMP TRAP notifications about suspicious sessions.
To configure the policy to send SNMPv3 TRAP notifications about suspicious sessions, follow the procedure:
Create a user for SNMPv3 service:
Select > .
Create a new one.
Enter Login.
Choose the
servicein the Role field.Select
Passwordin the Authentication Type field and provide your password.In the SNMP section, define the settings:
- Enable SNMP.
- Select
SHAorMD5in the Authentication Method field. - Select AES or DES in the Encryption field.
Click .
Configure SNMPv3 TRAP:
- Select >
- Scroll down to the Maintenance and supervision section
- Configure the SNMPv3 TRAP server address and port
- Select the user with
servicerole, created in step 1. - Click .
Create policy:
- Select > .
- Click .
- Provide the Name for the policy.
- Select the SNMP TRAP option in the Actions field.
- Select
AI modulein the Policy type field. - Select the option of the Threat Probability Threshold (e.g.
avg) and add its value (e.g.90%). - Click .
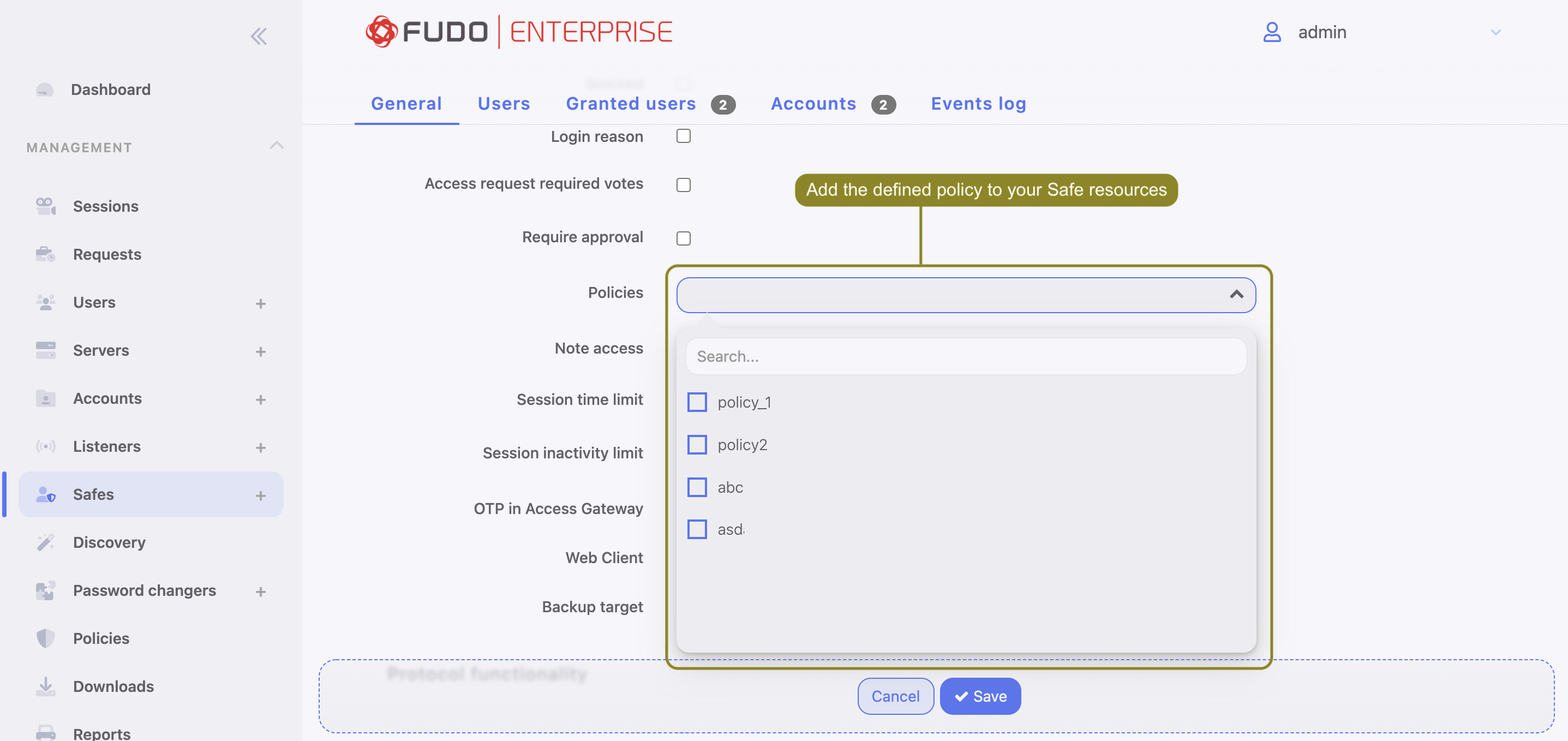
- Assign the policy to a safe that is used to establish connections to servers.
Click .
Example 2. Terminating suspicious sessions when the Threat Probability Threshold is reached.
To configure the policy to terminate suspicious sessions when the Threat Probability Threshold is reached, follow the procedure:
Create policy:
- Select > .
- Click .
- Provide the Name for the policy.
- Select the Terminate session option in the Actions field.
- Select
AI modulein the Policy type field. - Select the option of the Threat Probability Threshold (e.g.
avg) and add its value (e.g.90%). - Click .
Note
For harsh actions like pausing or terminating a session or blocking a user it’s advised to use higher max thresholds to minimize consequences of false positives.
- Assign the policy to a safe that is used to establish connections to servers.
Click .

Regular expression-based policy¶
Note
Fudo Enterprise supports POSIX extended regular expression.
Follow the steps to configure a regular expression-based policy:
- Select > .
- Select Regular expressions tab.
- Click .
- Enter pattern name.
- Define the pattern itself.
Note
- Patterns can be defined as regular expressions.
- Fudo Enterprise does not recognize expressions which use backslash character, e.g.
\d,\D,\w,\W.
- Repeat steps 3-5 to define additional patterns.
- Click .
Note
Regular expressions examples
Command rm
(^|[^a-zA-Z])rm[[:space:]]
Command rm -rf (also -fr; -Rf; -fR)
(^|[^a-zA-Z])rm[[:space:]]+-([rR]f|f[rR])
Command rm file
(^|[^a-zA-Z])rm[[:space:]]+([^[:space:]]+[[:space:]]*)?/full/path/to/a/file([[:space:]]|\;|$)
(^|[^a-zA-Z])rm[[:space:]]+.*justafilename
- Select > .
- Click .
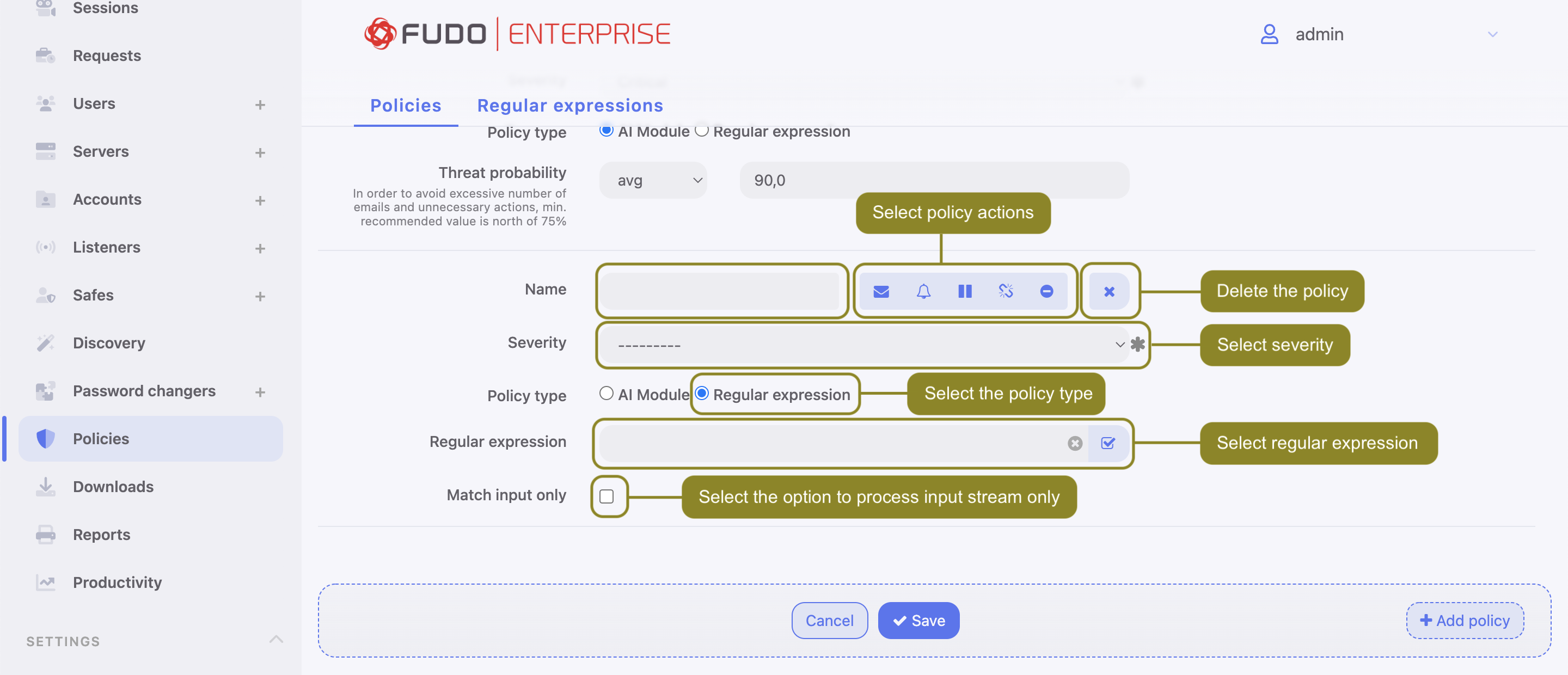
- Enter policy name.
- Select actions:
- - send email notification to system administrator.
Note
Sending email notifications requires configuring and enabling notification service as well as Session policy match notification enabled in safe configuration.
- - send SNMP TRAP notification to the receiver.
Note
Sending SNMP TRAP notifications requires configuring the SNMPv3 TRAP in the System tab. Check the SNMP page for more information.
- - pause connection.
- - terminate connection.
- - block user.
Note
Note that blocking the user automatically terminates the connection.
- Select
Regular expressionin the Policy type field. - Select monitored patterns.
- Select policy severity.
Note
Severity parameter value is included in the email notification message.
- Select the Match input only option to process input stream only.
Note
In RDP, VNC and MySQL protocols only input data is processed.
- Click .
- After defining a policy, assign it to a safe that is used to establish connections to servers.

Related topics: