Authentication¶
Fudo Enterprise has a broad spectrum of authentication methods for user’s authentication against the target server. Those are:
Mentioned authentication methods require defining connections to the external authentication servers.
External authentication server definition¶
To add an external CERB, Radius, Active Directory or LDAP authentication server, proceed as follows.
- Select > .
- Click .
- Select authentication service type:
CERB,Radius,Active DirectoryorLDAP. - Provide configuration parameters depending on selected external authentication system type.
- Click .
| Parameter | Description |
|---|---|
| CERB | |
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Bind address | IP address used for sending requests to given host. |
| Service | CERB service used for authenticating Fudo Enterprise users. |
| Secret | Secret used to establish server connection. |
| Second factor | Additional verification step with authentication methods OATH, SMS or DUO. |
| RADIUS | |
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Bind address | IP address used for sending requests to given host. |
| NAS ID | RADIUS server NAS-Identifier parameter. |
| Secret | Secret used to establish server connection. |
| Repeat secret | Repeat secret used to establish server connection. |
| Second factor | Additional verification step with authentication methods OATH, SMS or DUO. |
| LDAP | |
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Bind address | IP address used for sending requests to given host. |
| Bind DN | Template containing a path which will be used to create queries to LDAP server. |
| Encrypted connection | This option is required to be checked for the domain users who change their passwords in the Access Gateway. |
| Server certificate | LDAP server certificate. |
| Second factor | Additional verification step with authentication methods OATH, SMS or DUO. |
| Active Directory | |
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Bind address | IP address used for sending requests to given host. |
| Active Directory domain | Domain which will be used for authenticating users in Active Directory. |
| Encrypted connection | This option is required to be checked for the domain users who change their passwords in the Access Gateway. |
| Server certificate | Active Directory server certificate. |
| Login | The privileged account’s login name to modify a user password on the Active Directory server. |
| Secret | Secret used to establish server connection to modify a user password on the Active Directory server. |
| Repeat secret | Secret used to establish server connection to modify a user password on the Active Directory server. |
| Second factor | Additional verification step with authentication methods OATH, SMS or DUO. |
Warning
When additional authentication method (OATH, SMS or DUO) is selected as a Second factor for synchronization with External authentication server (AD / LDAP / CERB / RADIUS), it won’t be enough to just select one of the External authentication server source within the User definition. The additionally selected authentication method should be configured within the User definition as a primary authentication method. Then users’ authentication methods will be automatically synchronized according to External authentication server settings.
Note
Labeled IP addresses
In case of cluster configuration, select a labeled IP address from the Bind address drop-down list and make sure that other nodes have IP addresses assigned to this label. For more information refer to the Labeled IP addresses topic.
OATH authentication definition¶
Refer to the Two-factor OATH authentication with Google Authenticator page.
SMS authentication definition¶
- Select > .
- Choose SMS Authentication tab.
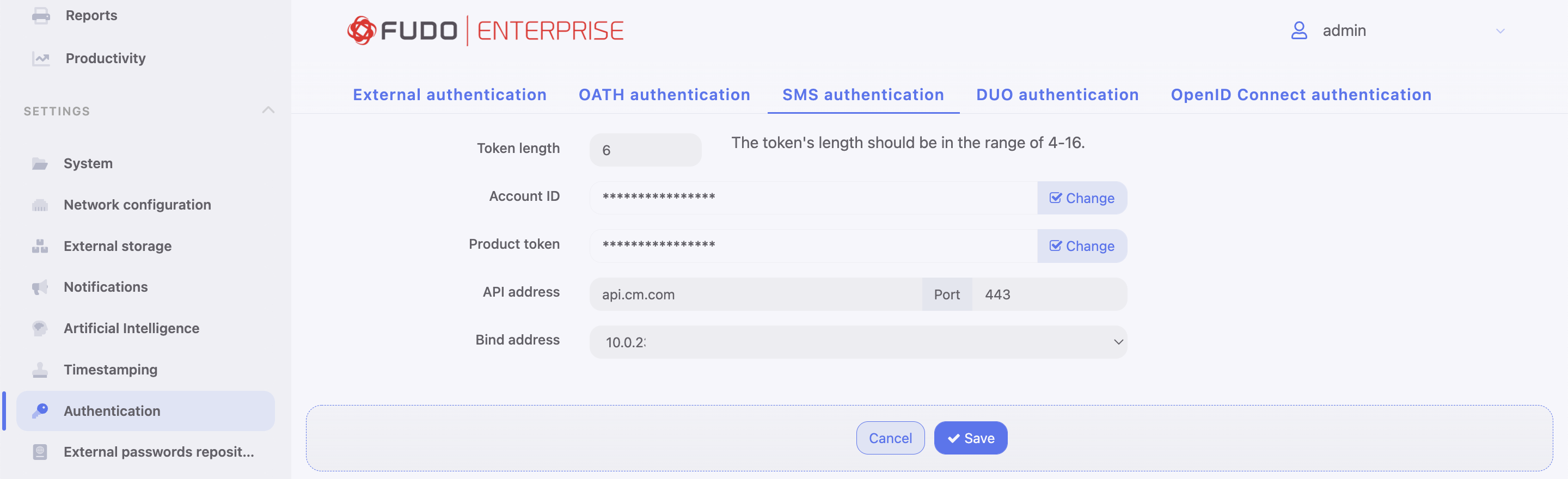
- Input Token length.
Note
The token’s length should be in the range of 4-16.
- Input Account ID.
- Input Product token.
- Input API address and its port.
Note
The values for Account ID, Product token and API address are given by CM.COM service. You need to have a registered account there to be able to obtain the required information.
- Select the Bind address.
- Click .
Configure SMS authentication method for the User:
- Go to > .
- Find and select the user for whom you want to enable SMS authentication.
- Input a phone number in the Phone input field.
- Under the Authentication section choose Type:
SMS. - From a First factor drop-down list choose
Static passwordorExternal authentication(AD or LDAP).
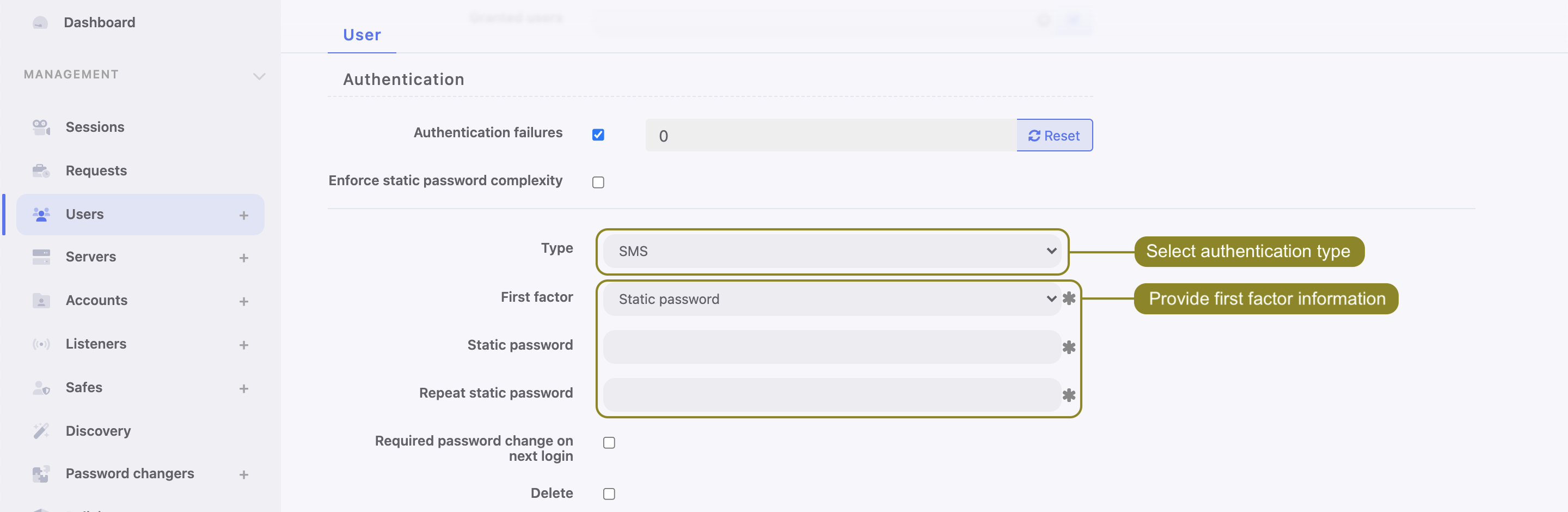
- Click .
- Log in to the Access Gateway with SMS code.
DUO authentication definition¶
- Download and install Duo Mobile phone application.
- Sign up for a personal account on Duo Security.
- Select > .
- Choose DUO Authentication tab.

- Input from the personal Duo Security profile: API address, Integration key and Secret key.
- Select the Bind address.
- Click .
Configure DUO authentication method for the User:
- Go to > .
- Find and select the user for whom you want to enable DUO authentication.
- Under Authentication section choose Type:
DUO. - From a First factor drop-down list choose
Static passwordorExternal authentication(AD or LDAP). - Input DUO username.
- Input DUO user id.
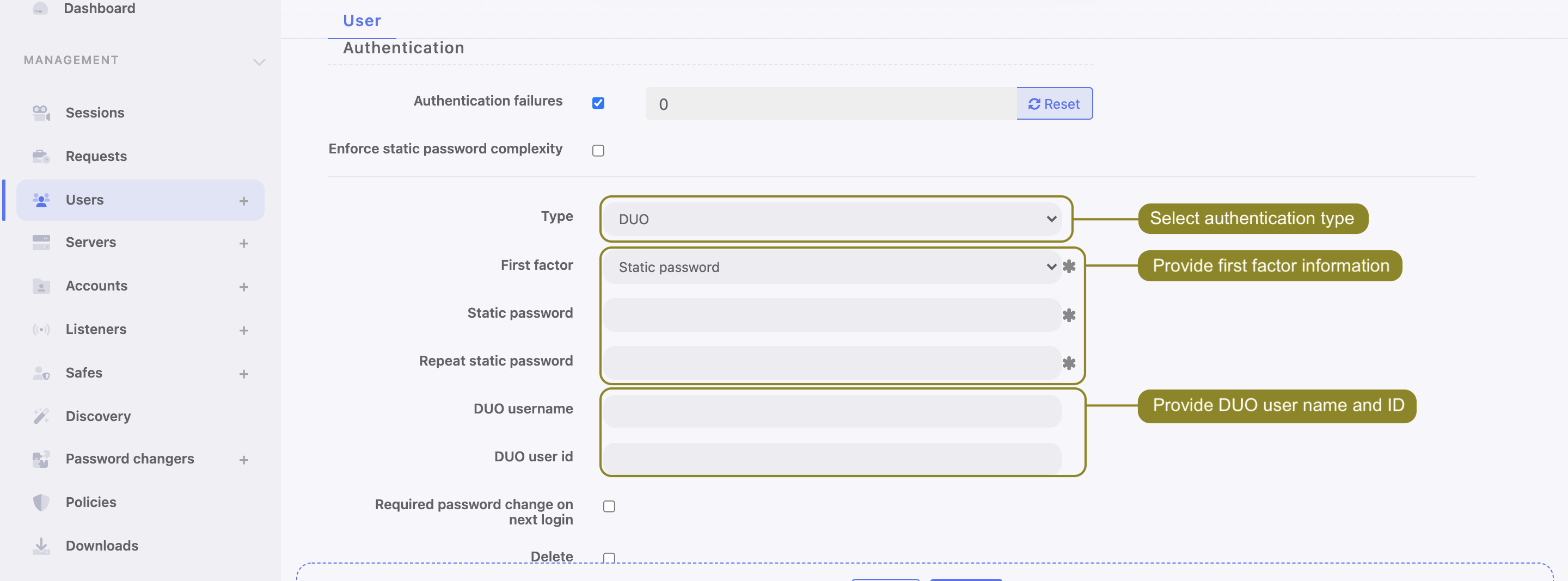
- Click .
- Log in to the Access Gateway by tapping Accept on push notification from Duo Mobile application.
OpenID Connect authentication definition¶
This authentication method is configured globally and is not tied to any particular user. Thus even if a user has no authentication methods configured, they can authenticate using OpenID Connect in Access Gateway and Admin Panel.
Follow the steps to configure the OpenID Connect authentication method:
- Select > .
- Choose OpenID Connect authentication tab.
- Click .
- Check the Enabled option to globally enable OpenID Connect authentication.
- Provide Name (
Azure,Oktaor any other Identity Provider). - Input Configuration URL.
Note
This URL is specific for every Identity Provider and allows identifying one for correct configuration. Example of Configuration URL for Google: https://accounts.google.com/.well-known/openid-configuration.
- Provide Client ID, Client secret. Those values are available after the registration on selected provider.
- Add Username mapping and Email mapping. Those fields are useful when user’s name has different naming convention.
- Provide Bind address.
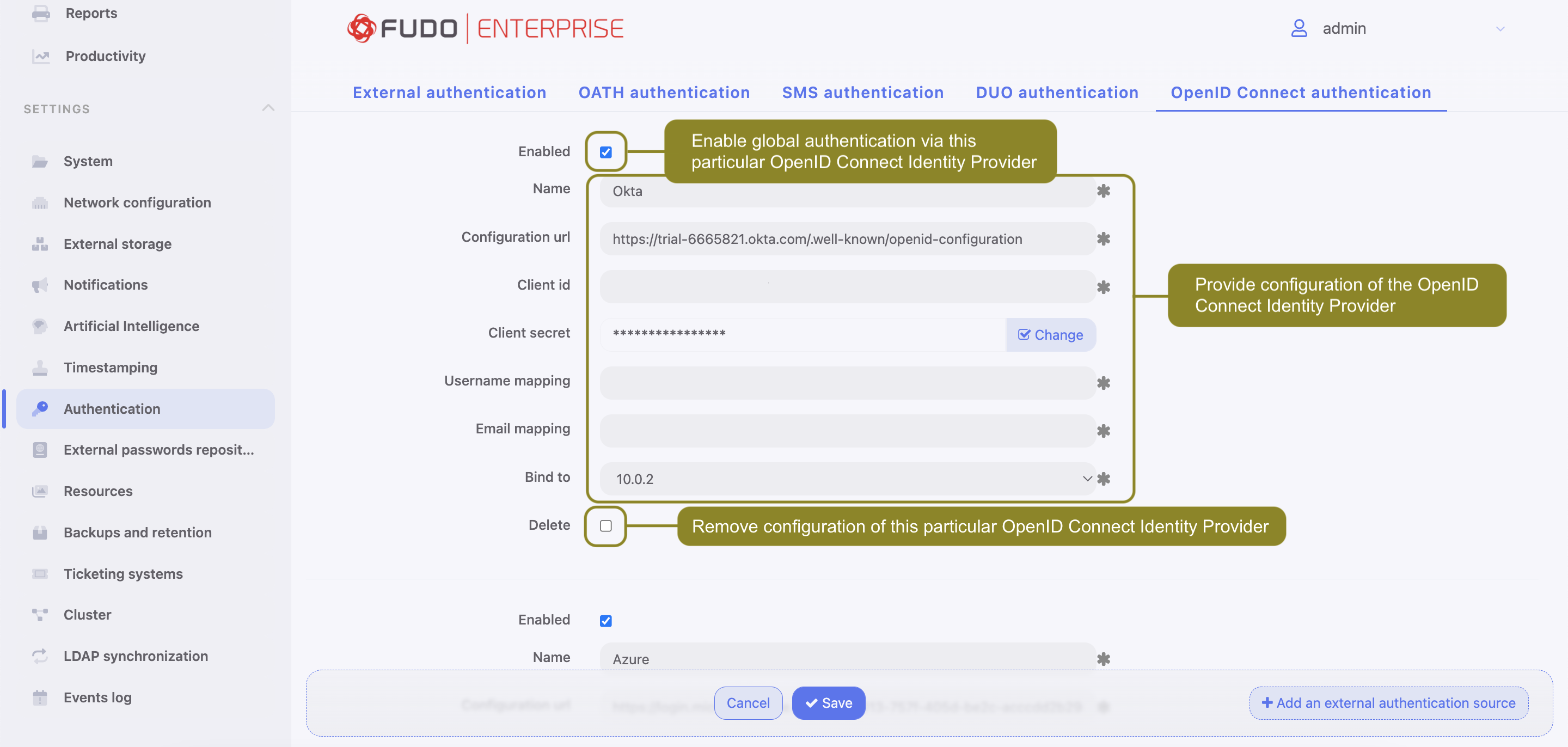
- Click .
Note
The algorithm to determine the user’s identity is following:
- If Username mapping is defined, we try to find field in the data with that name. If JSON data contains this field, we will try to find user by this name.
- If Username mapping is not defined, the field is not found in the data or the user is not found by name, we check if Email mapping is defined. If it is defined and exists in JSON data, we try to find user by this email.
- When neither Username mapping nor Email mapping is defined we try to find the user by his name or his email by looking for those fields in the data in the following order: email, upn, unique_name.
Furthermore, if the
email_verificationfield is present in the data, it must be set totrue.
Log in using the defined authentication method:
Related topics: