SSH in bastion mode¶
This chapter contains an example of a basic Fudo PAM configuration, to monitor SSH access in bastion mode.
In this scenario, the user connects to the remote server over the SSH protocol and logs in to the Fudo PAM using an individual login and password combination (john_smith/john). The user specifies account on a target server in the login string (john_smith#admin_ssh_server) and connects to it over default SSH port number. Upon establishing connection, login credentials are substituted with the previously defined values: root/password (authentication modes are described in the User authentication modes section).

Prerequisites¶
Description below assumes that the system has been already initiated. The initiation procedure is described in the System initiation topic.
Configuration¶

Adding a server
is a definition of the IT infrastructure resource, which can be accessed over one of the specified protocols.
- Select > .
- Click and select Static server.
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | ssh_server |
| Description |  |
| Blocked |  |
| Protocol | SSH |
| Legacy ciphers |  |
| Bind address | Any |
| Permissions | |
| Granted users |  |
| Server addresses | |
| IP address | 10.0.150.1 |
| Port | 22 |
- Click i to download the target server’s public key.
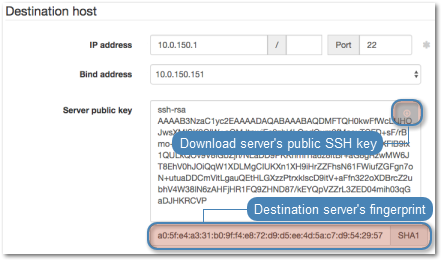
- Click .
Adding a user
User defines a subject entitled to connect to servers within monitored IT infrastructure. Detailed object definition (i.e. unique login and domain combination, full name, email address etc.) enables precise accountability of user actions when login and password are substituted with a shared account login credentials.
- Select > .
- Click .
- Provide essential user information:
| Parameter | Value |
|---|---|
| General | |
| Login | john_smith |
| Fudo domain |  |
| Blocked |  |
| Account validity | Indefinite |
| Role | user |
| Preferred language | English |
| Safes |  |
| Full name | John Smith |
john@smith.com |
|
| Organization |  |
| Phone |  |
| AD Domain |  |
| LDAP Base |  |
| Permissions | |
| Granted users |  |
| Authentication | |
| Authentication failures |  |
| Enforce static password complexity |  |
| Type | Password |
| Password | john |
| Repeat password | john |
- Click .
Adding a listener
determines server connection mode (proxy, gateway, transparent, bastion) as well as its specifics.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | ssh_listener |
| Blocked |  |
| Protocol | SSH |
| Legacy ciphers |  |
| Case insensitivity |  |
| Permissions | |
| Granted users |  |
| Connection | |
| Mode | bastion |
| Local address | 10.0.150.151 |
| Port | 22 |
| External address |  |
| External port |  |
- Click i to generate the proxy server’s private key or i to upload the .PEM file private key definition.
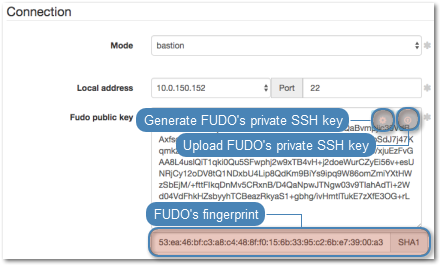
Note
For security reasons the form displays server’s public key derived from the generated or uploaded private key.
- Click .
Adding an account
defines the privileged account existing on the monitored server. It specifies the actual login credentials, user authentication mode: anonymous (without user authentication), regular (with login credentials substitution) or forward (with login and password forwarding); password changing policy as well as the password changer itself.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | admin_ssh_server |
| Blocked |  |
| Account type | regular |
| Session recording | all |
| Notes |  |
| Data retention | |
| Override global retention settings |  |
| Delete session data after | 61 days |
| Permissions | |
| Granted users |  |
| Server | |
| Server | ssh_server |
| Credentials | |
| Domain |  |
| Login | root |
| Replace secret with | with password |
| Password | password |
| Repeat password | password |
| Password change policy | Static, without restrictions |
- Click i to generate the proxy server’s private key or i to upload the .PEM file private key definition.
Note
For security reasons the form displays server’s public key derived from the generated or uploaded private key.
- Click .
Defining a safe
directly regulates user access to monitored servers. It specifies available protocols’ features, policies and other details concerning users and servers relations.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | ssh_safe |
| Notifications |  |
| Login reason |  |
| Require approval |  |
| Policies |  |
| Note access | No access |
| Protocol functionality | |
| RDP |  |
| SSH |  |
| VNC |  |
- Select Users tab.
- Click .
- Find John and click ..
- Click .
- Select Accounts tab.
- Click .
- Find the
admin_ssh_serverobject and click .. - Click .
- Click in the Listeners column.
- Find the
ssh_listenerobject and click .. - Click .
- Click .
Establishing connection¶
PuTTY - SSH client for Microsoft Windows
- Download and launch PuTTY.
- In the Host Name (or IP address) field, enter
10.0.150.151. - Select the
SSHconnection type and leave the default port number unchanged.
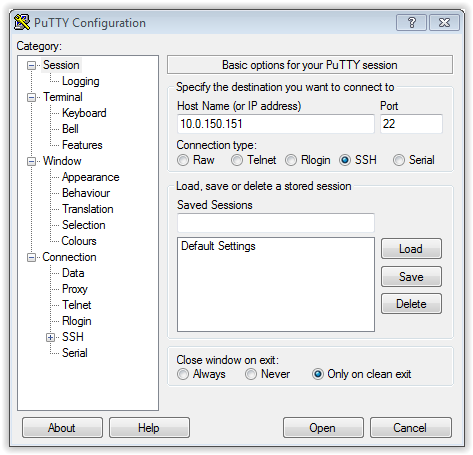
- Click Open.
- Enter user name along with the account name on the target host.
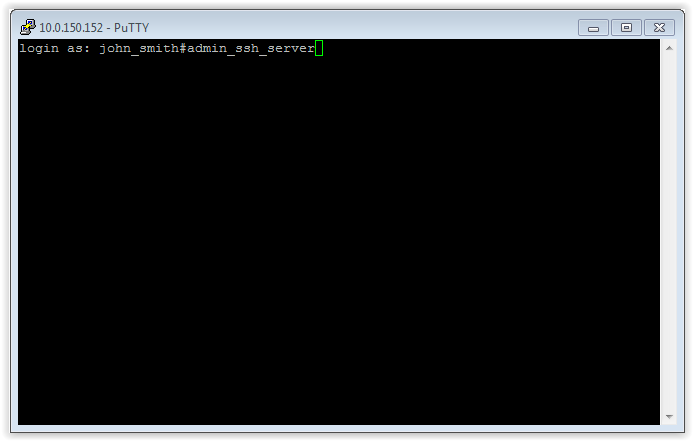
Note
Alternatively, instead of the account name, you can specify the server by its name john_smit#ssh_server.
- Enter password.
Command line interface
Launch terminal and run ssh command:
ssh john_smith#admin_ssh_server@10.0.150.151
Note
Due to special interpretation of the \ character by different system shells (e.g. bash), user login and domain combination require specific formatting:
- “domain\user”#bsd01@10.0.60.138
- ‘domain\user’#bsd01@10.0.60.138
- domain\user#bsd01@10.0.60.138
Viewing user session¶
- Open a web browser and go to the
10.0.150.150web address. - Enter the login and password to login to the Fudo PAM administration panel.
- Select > .
- Find John Smith’s session and click i.
Related topics: