Users synchronization¶
User is one of the fundamental data model entity. Only defined users are allowed to connect to monitored servers. Fudo PAM features automatic users synchronization service which enables importing users information from Active Directory servers or other servers compatible with the LDAP protocol.
Warning
It is required that LDAP server supports a memberOf parameter - an attribute that specifies the distinguished names of the groups to which this object belongs.
New users definitions and changes in existing objects are imported from the directory service periodically every 5 minutes. Deleting a user object from an AD or an LDAP server requires performing the full synchronization to reflect those changes on Fudo PAM. The full synchronization process is triggered automatically once a day at 00:00, or can be triggered manually.
- Fudo PAM supports nested LDAP groups.
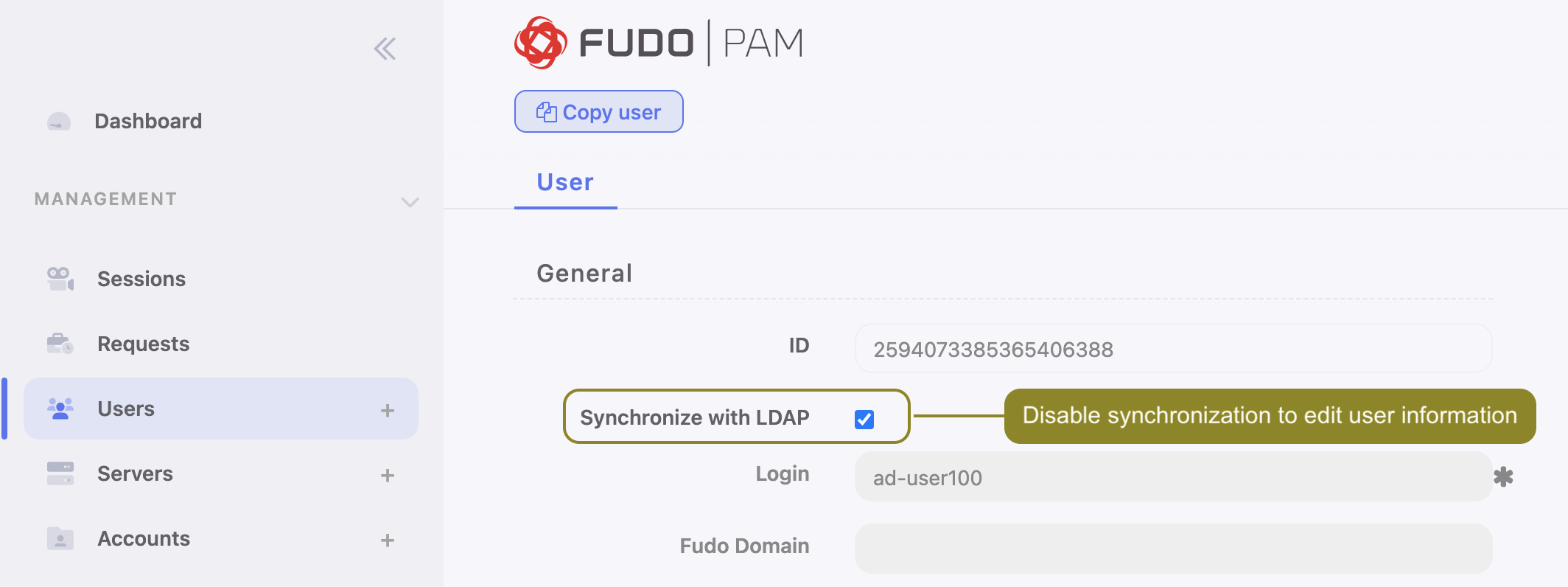
- Also, Fudo PAM allows synchronizing the user’s data with the LDAP service source. The
Synchronize with LDAPoption is responsible for this process. When this option is checked for the given user, an administrator can’t edit the user’s data manually but can add or edit their authentication methods. If theSynchronize with LDAPoption is unchecked, the user is no longer synchronized with LDAP source, and can be edited by an administrator. The administrator can still check the option and reinstate synchronization with LDAP, but any change made manually will disappear with the next synchronisation attempt. Only the added authentication methods won’t change.
Configuring users synchronization service
To enable users synchronization feature, proceed as follows.
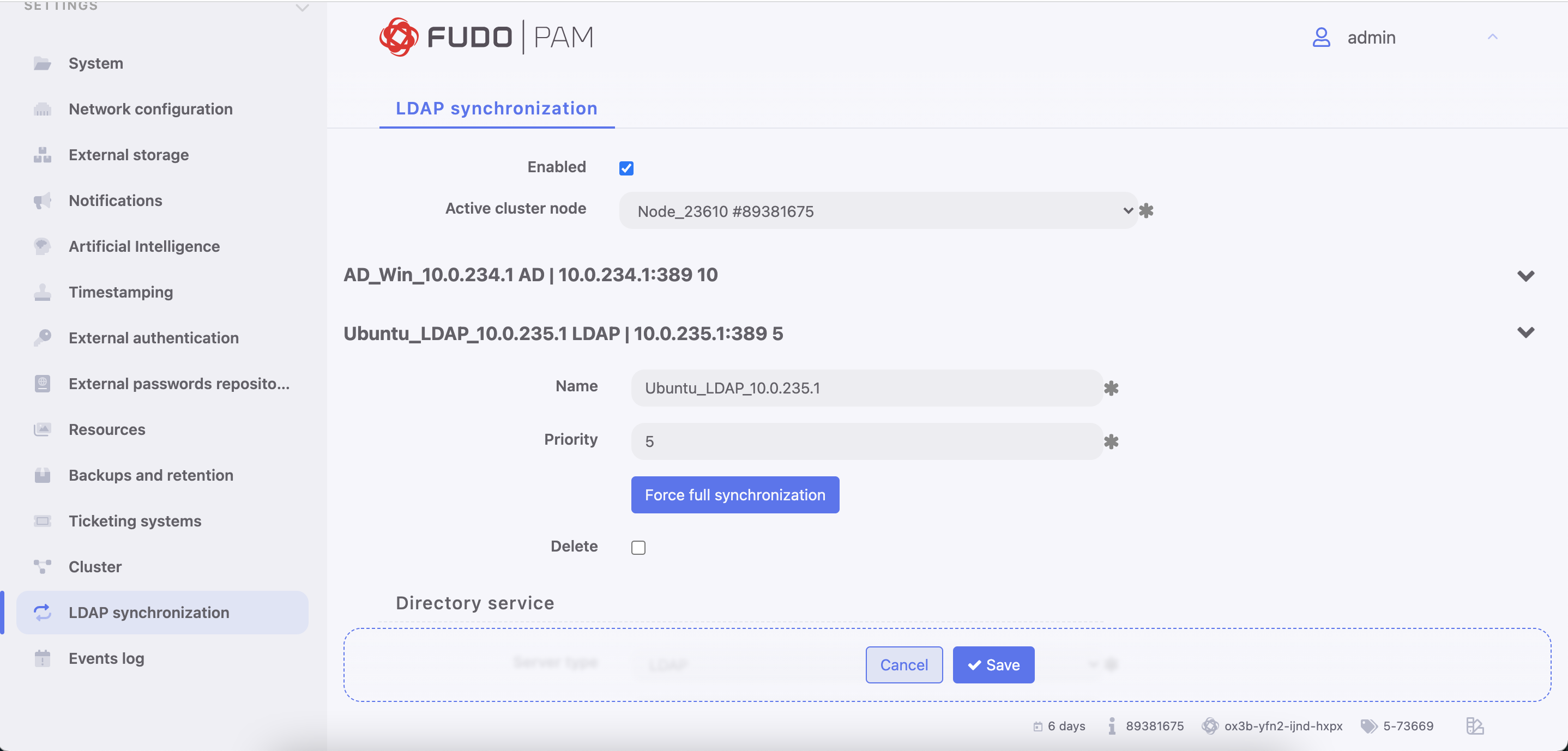
- Select > .
- Select Enabled.
- In case of cluster configuration, from the Active cluster node drop-down list, select which node will be performing objects synchronization with LDAP service.
- Click .
- Provide domain’s name.
- Define priority, determining the order in which domains are queried.
Note
Lower number translates to higher priority.
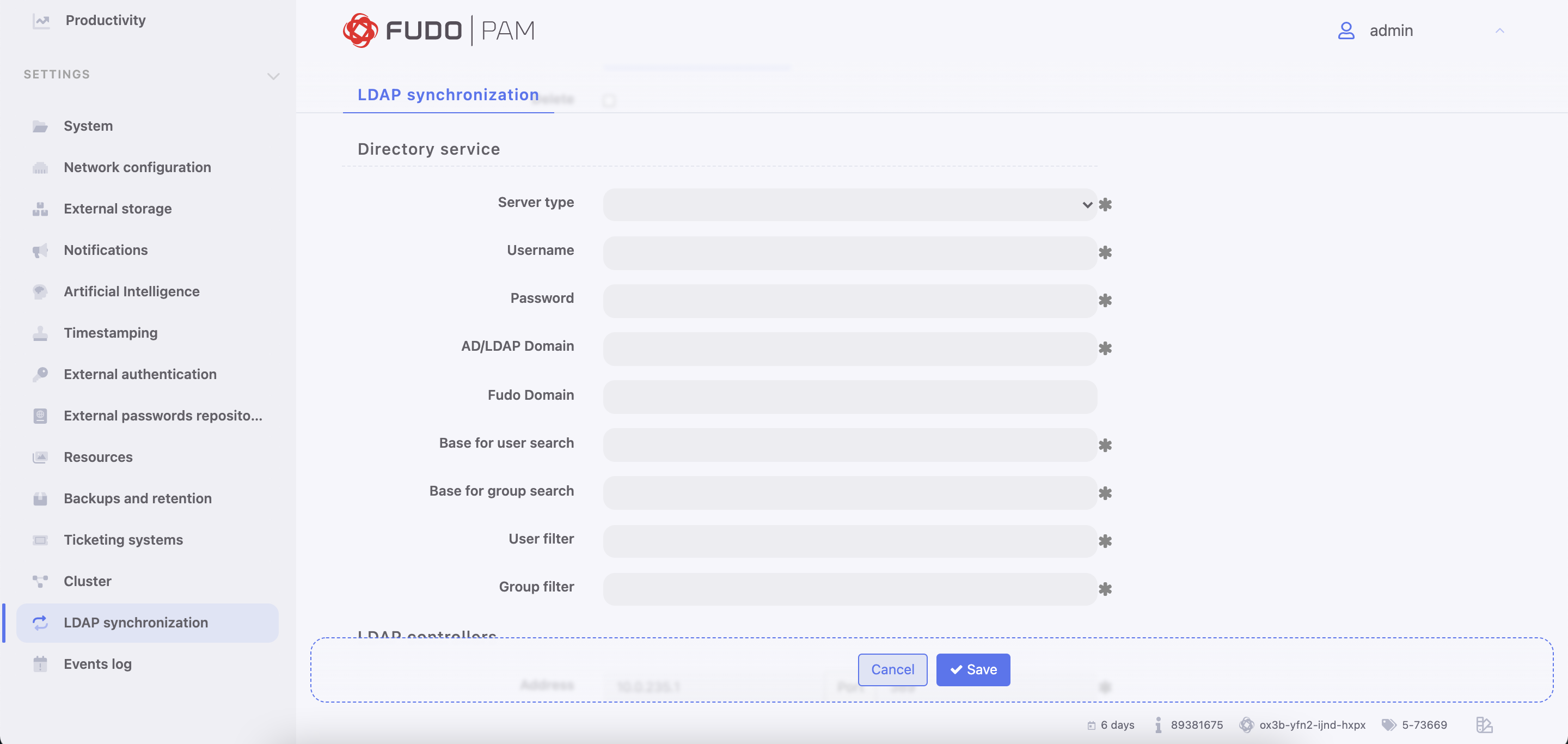
- In the Directory service section, select data source type from the Server type drop-down list.
- Provide the user authentication information to access user data on given server.
- Enter domain name, to which imported users are assigned to.
- Provide base DN parameter for users’ objects (eg.
DC=devel,DC=whl). - Provide base DN for parameter groups’ objects (eg.
DC=tech,DC=whl).
Note
DN parameter should not contain any white space characters.
- Define filter (or leave the default value) for user records, which are subject to synchronization.
- Define filter (or leave the default value) for user groups, which are subject to synchronization.
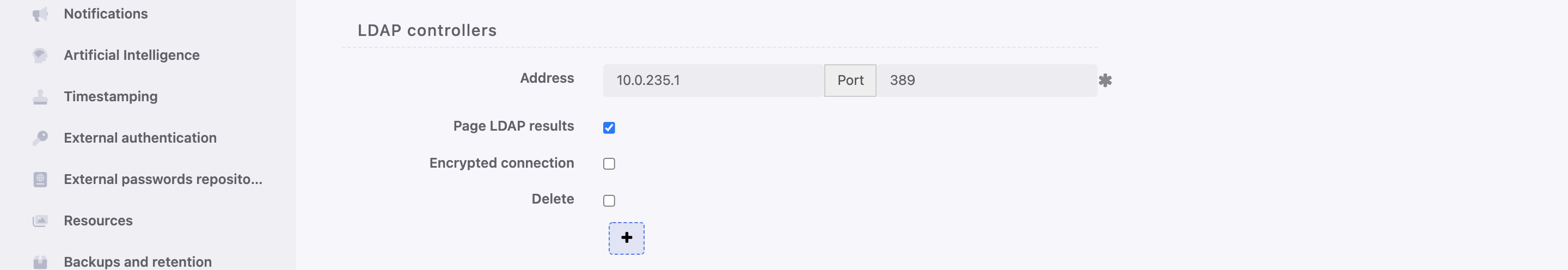
- Click i in the LDAP controllers section to define directory service server.
- Provide IP address and port number.
Note
In case of TLS-encrypted connection, define LDAP server’s address using its full domain name (e.g. tech.ldap.com) instead of an IP address, to ensure the certificate is verified properly. Make sure that the given server name is included in certificate’s Common Name field.
- Select the Page LDAP results option to enable paging.
- Select the Encrypted connection option to enable encryption and upload the CA certificate.
Note
Click i to add more directory servers.
- Define user information mapping.
Note
Fields mapping enables importing users information from nonstandard attributes, e.g. telephone number defined in an attribute named mobile instead of the standard telephoneNumber.
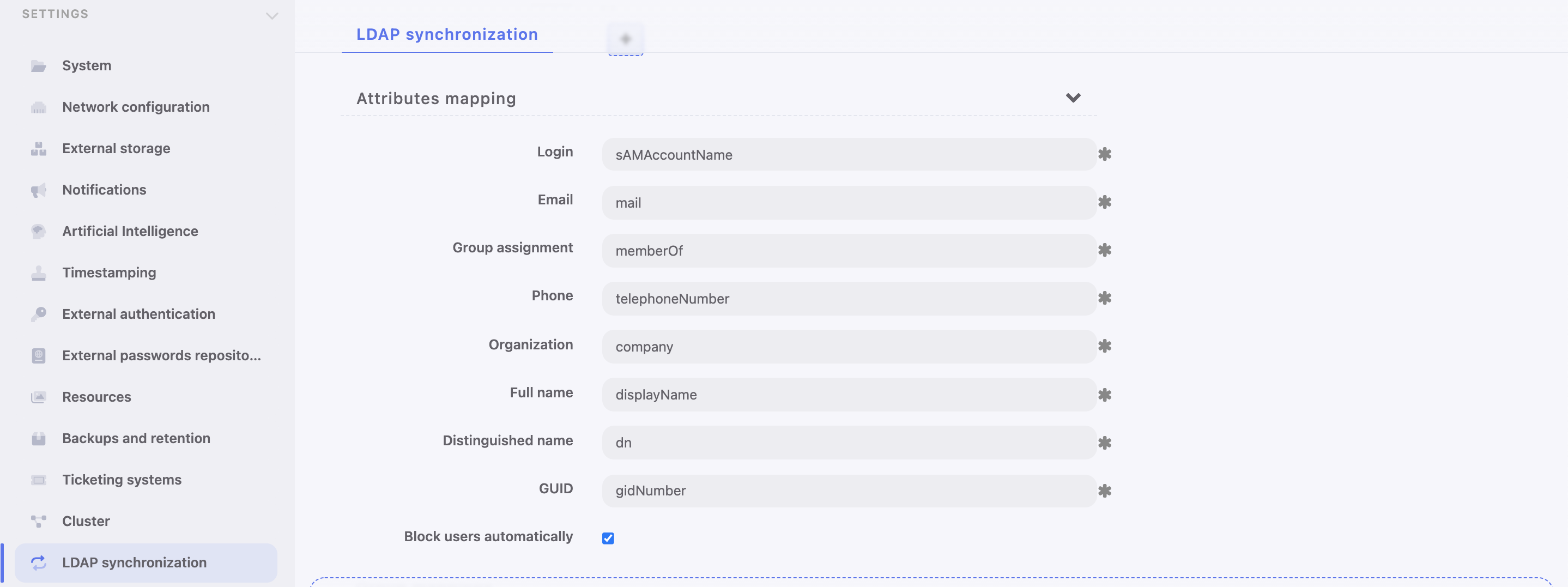
- Select Block automatically to automatically block local users’ accounts blocked in the directory.
- Click i in the Groups mapping section to define user groups to safes assignment.
- Type in user group and select desired entry.
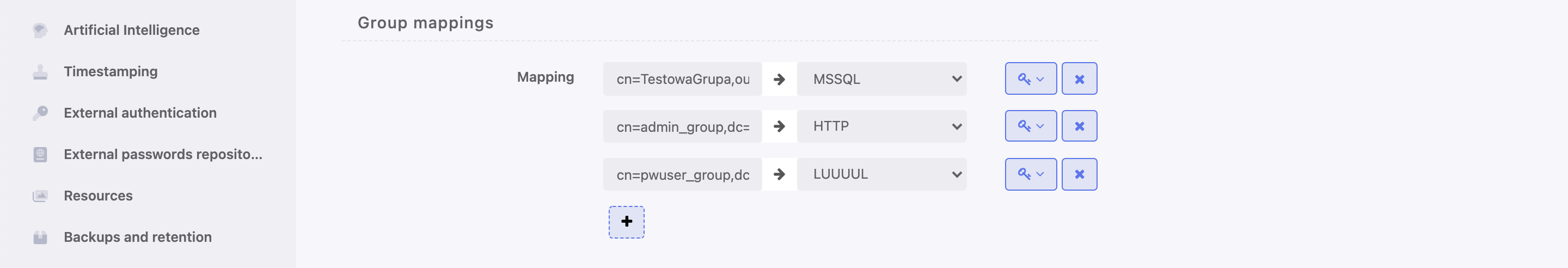
- Assign safes to user groups.
- Assign external authentication sources to user groups.
Note
External authentication sources are assigned to users in the exact sequence they are defined in groups mapping. Thus if the same user is present in more than one group, Fudo PAM will be authenticating him against external authentication sources starting from those defined in the first group mapping defined.
For example:
A user is assigned to groups A and B. Group B is mapped to Safe RDP and has CERB and Radius authentication sources assigned. Group A is second in order and it is mapped to Safe SSH and has AD authentication source assigned.
Authenticating a user, Fudo PAM will send requests to external authentication sources in the following order:
- CERB.
- Radius.
- AD.
- Click .
Note
- The option enables processing changes in directory structures which cannot be processed during periodical synchronization, eg. deleting a defined group or deleting a user.
- The full synchronization process is triggered automatically once a day at 00:00, or can be triggered manually.
- Use diagnostics tools to troubleshoot problems with LDAP configuration.
- Fudo PAM supports nested LDAP groups.
Related topics: