External authentication¶
Some of the authentication methods, require defining connections to external authentication servers. Those are:
Authentication servers configuration page enables adding new and editing existing authentication servers.
To open the authentication servers configuration page, select > .
New external authentication server definition¶
To add an external authentication server, proceed as follows.
- Select > .
- Click .
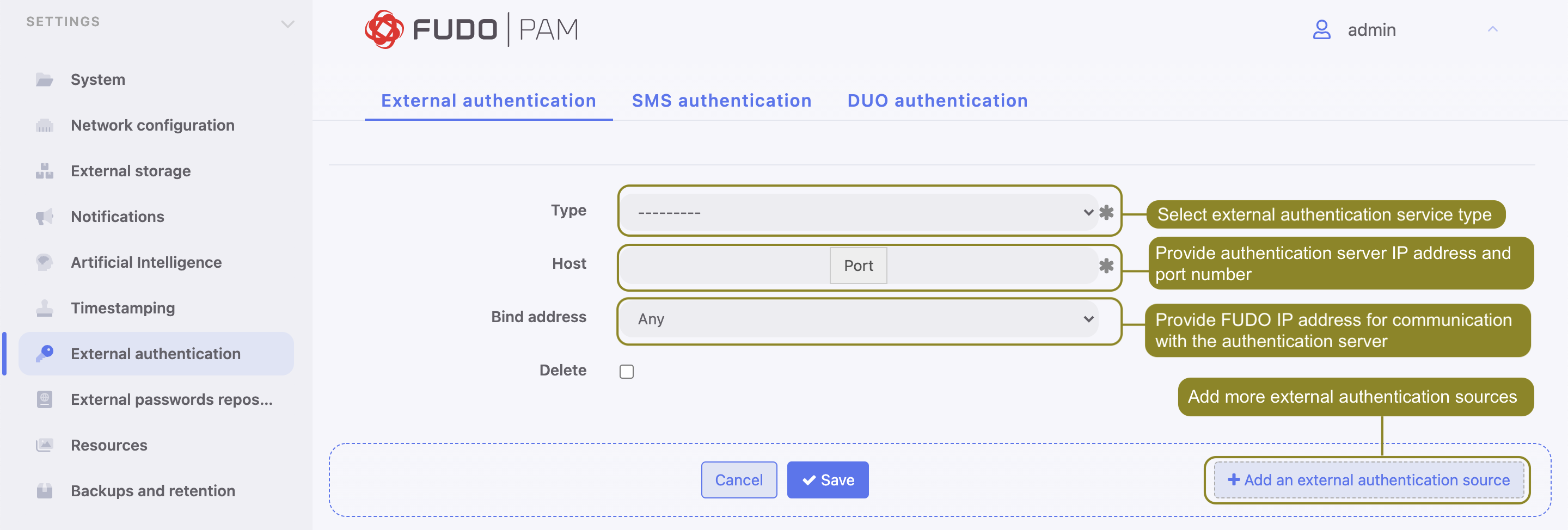
- Select authentication service type.
- Provide configuration parameters depending on selected authentication system type.
| Parameter | Description |
|---|---|
| CERB | |
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Bind address | IP address used for sending requests to given host. |
| Secret | Secret used to establish server connection. |
| Service | CERB service used for authenticating Fudo PAM users. |
| RADIUS | |
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Bind address | IP address used for sending requests to given host. |
| Secret | Secret used to establish server connection. |
| NAS ID | RADIUS server NAS-Identifier parameter. |
| LDAP | |
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Bind address | IP address used for sending requests to given host. |
| Bind DN | Template containing a path which will be used to create queries to LDAP server. |
| Active Directory | |
| Host | Server’s IP address. |
| Port | Port used to establish connections with given server. |
| Bind address | IP address used for sending requests to given host. |
| Active Directory domain | Domain which will be used for authenticating users in Active Directory. |
| Encrypted connection | This option is required to be checked for the domain users who change their passwords in the User Portal (Access Gateway). |
| Server certificate | Active Directory server certificate. |
| Login | The privileged account’s login name to modify a user password on the Active Directory server. |
| Secret | Secret used to establish server connection to modify a user password on the Active Directory server. |
| Repeat secret | Secret used to establish server connection to modify a user password on the Active Directory server. |
Note
Labeled IP addresses
In case of cluster configuration, select a labeled IP address from the Bind address drop-down list and make sure that other nodes have IP addresses assigned to this label. For more information refer to the Labeled IP addresses topic.
- Click .
Editing authentication server definition
To edit an authorization server definition, proceed as follows.
- Select > .
- Find the server definition and change its configuration as desired.
- Click .
Deleting authentication server definition
To delete authentication server definition, proceed as follows.
- Select > .
- Find desired server definition and select Delete.
- Click .
SMS authentication definition¶
- Select > .
- Choose SMS Authentication tab.
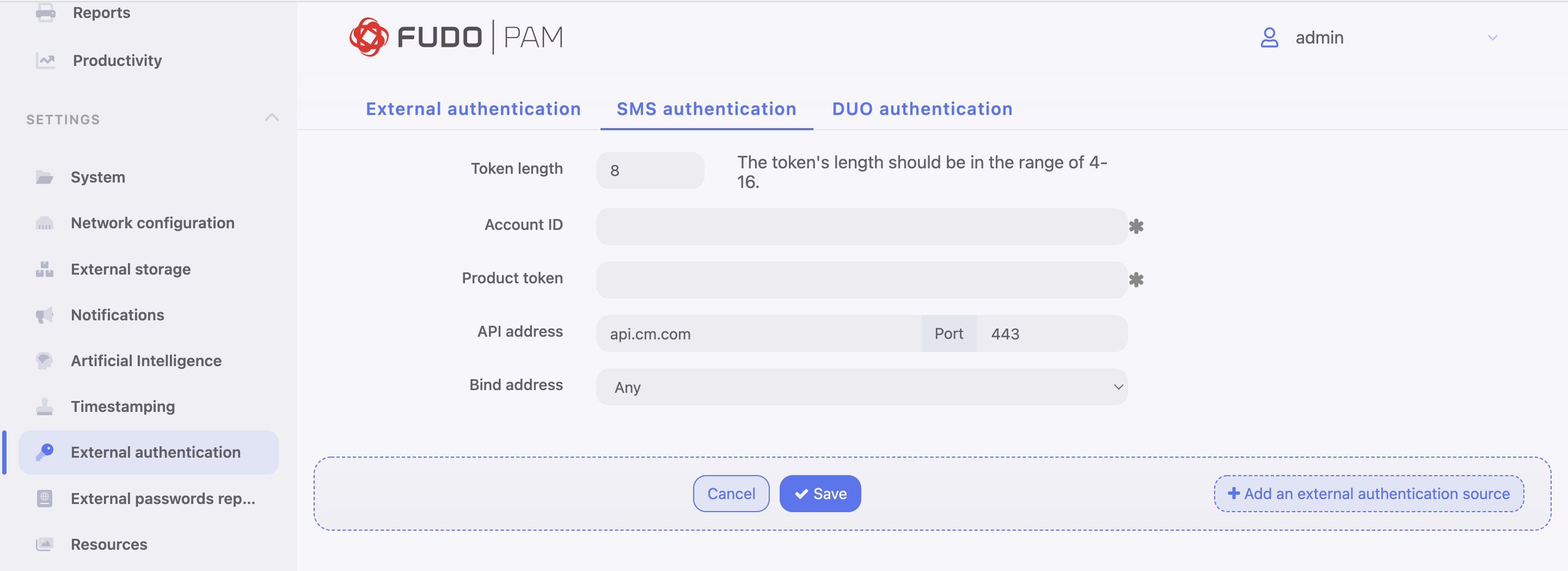
- Input Token length.
Note
The token’s length should be in the range of 4-16.
- Input Account ID.
- Input Product token.
- Input API address and its port.
Note
The values for Account ID, Product token and API address are given by CM.COM service. You need to have a registered account there to be able to obtain the required information.
- Select the Bind address.
- Click .
- Go to > .
- Find and select the user for whom you want to enable SMS authentication.
- Input a phone number in the Phone input field.
- Under the Authentication section choose Type:
SMS. - From a First factor drop-down list choose
Static passwordorExternal authentication(AD or LDAP).
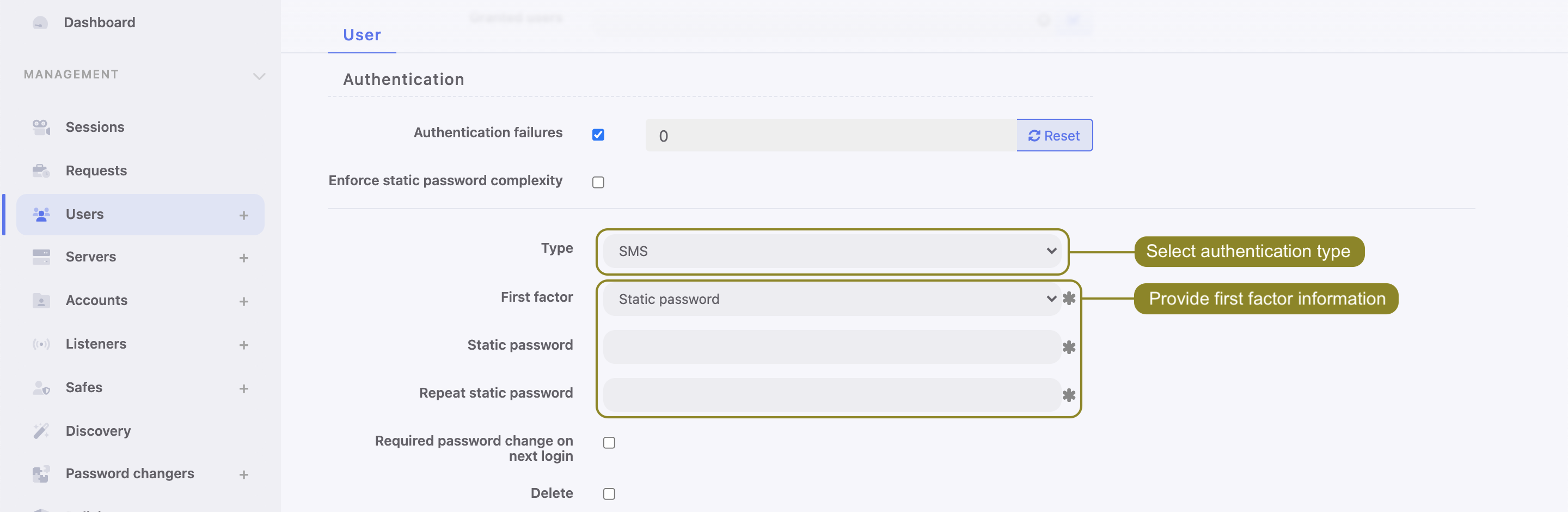
- Click .
- Log in to the User Portal (Access Gateway) with SMS code.
DUO authentication definition¶
- Download and install Duo Mobile phone application.
- Sign up for a personal account on Duo Security.
- Select > for DUO Authentication configuration.
- Choose DUO Authentication tab.
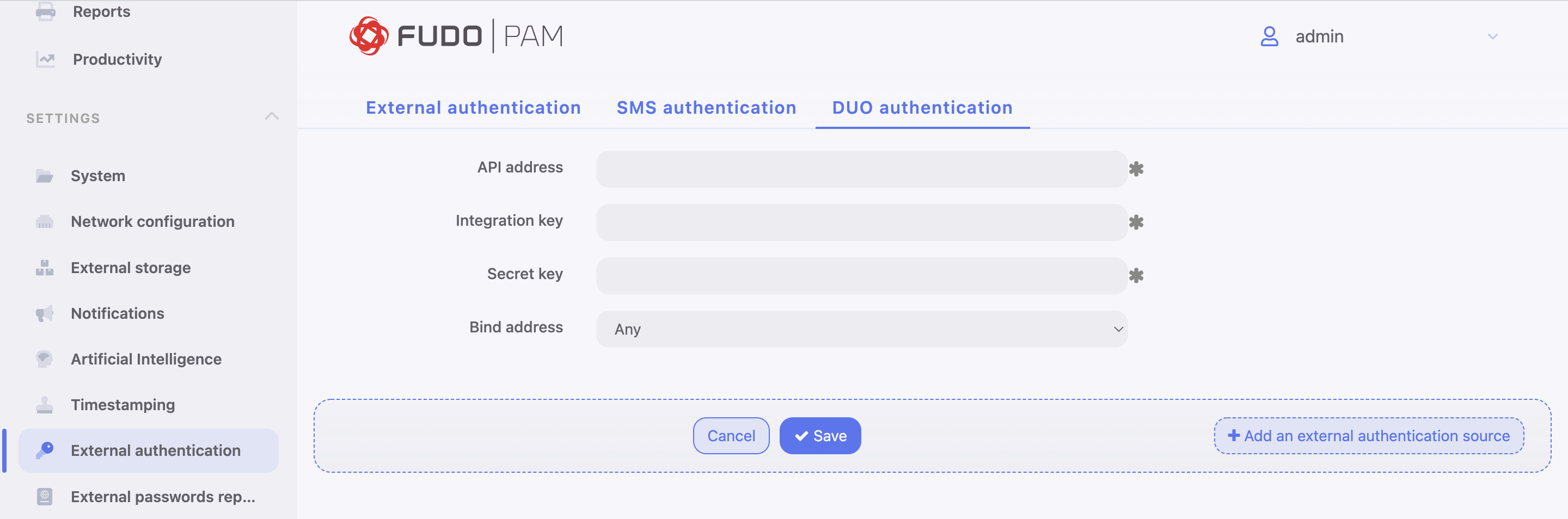
- Input from the personal Duo Security profile: API address, Integration key and Secret key.
- Select the Bind address.
- Click .
- Go to > .
- Find and select the user for whom you want to enable DUO authentication.
- Under Authentication section choose Type:
DUO. - From a First factor drop-down list choose
Static passwordorExternal authentication(AD or LDAP). - Input DUO username.
- Input DUO user id.
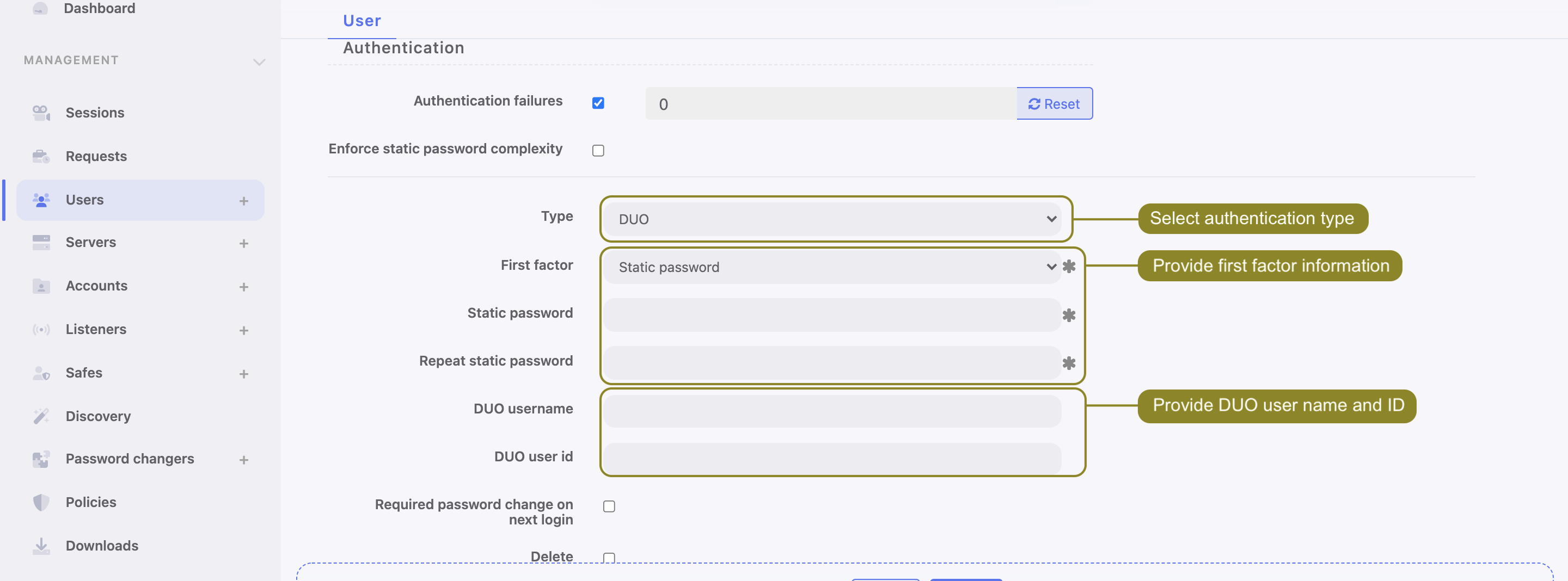
- Click .
- Log in to the User Portal (Access Gateway) by tapping Accept on push notification from Duo Mobile application.
Azure authentication definition¶
This authentication method is configured globally and is not tied to the particular user. So even if the user has no authentication methods at all, they can still authenticate using OpenID Connect in Access Gateway and Panel Admin.
Follow the steps to configure the Azure authentication method:
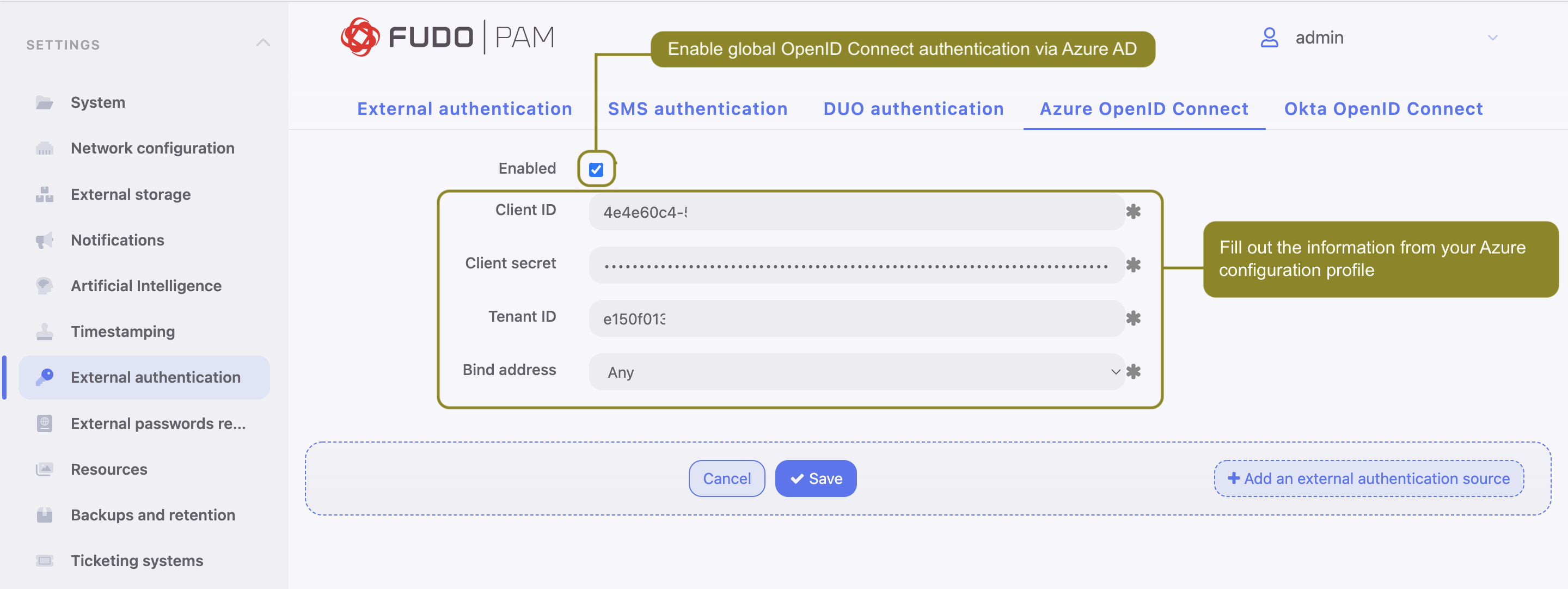
- Select > .
- Choose Azure OpenID Connect tab.
- Check the Enabled option to globally enable OpenID Connect authentication via Azure AD.
Warning
It is crucial to configure allowed redirect URL in your Azure application profile. Such URLs should point to the /oidc path on the host addresses used by Admin Panel and Access Gateway. For example,
https://mgmt.fudo/oidc
https://10.10.0.1/oidc
https://ag.fudo/oidc
- Provide information from your Azure application profile:
- Input Client ID. This is Application (client) ID from application configuration.
- Input Client secret, which is the Client secret from application configuration.
- Input Tenant ID - Directory (tenant) ID from application configuration.
Note
Values for those fields come from your Azure application profile.
- Select Bind address to bind to while connecting to Azure AD.
- Click .
Okta authentication definition¶
This authentication method is configured globally and is not tied to the particular user. So even if the user has no authentication methods at all, they can still authenticate using OpenID Connect in Access Gateway and Panel Admin.
Follow the steps to configure the Okta authentication method:
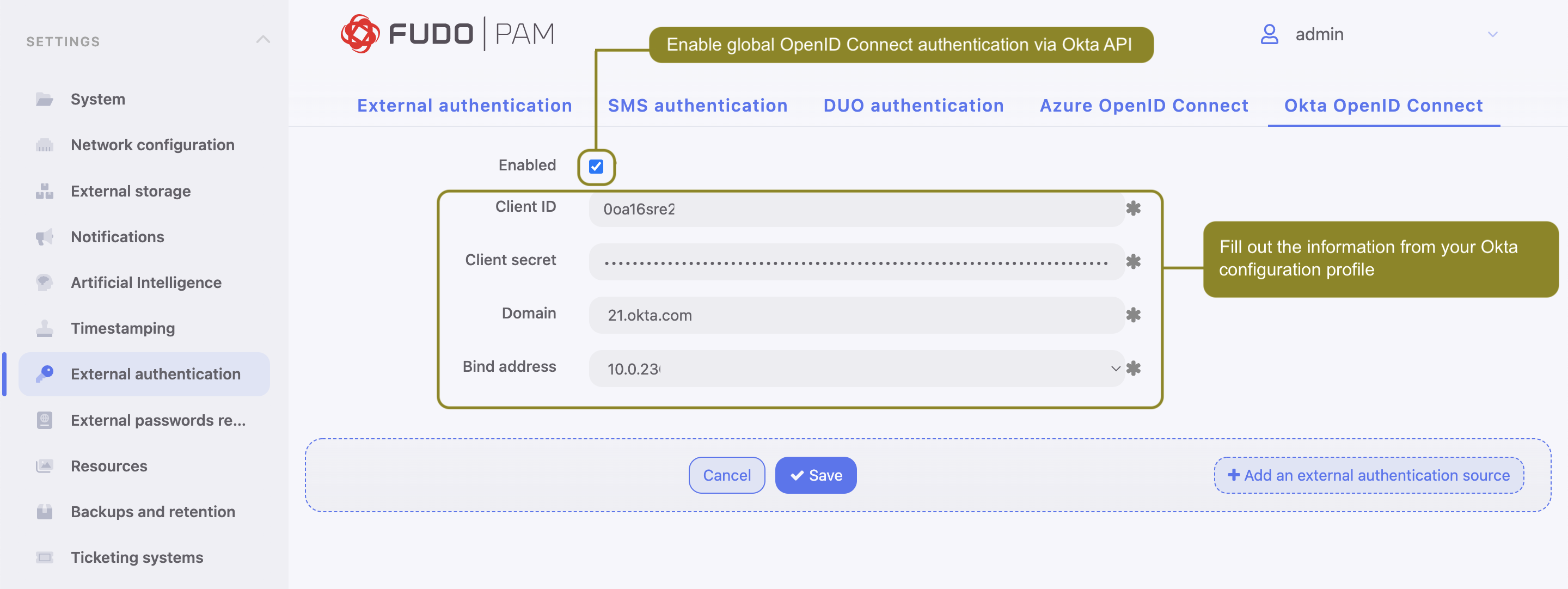
- Select > .
- Choose Okta OpenID Connect tab.
- Check the Enabled option to globally enable OpenID Connect authentication via Okta.
Warning
It is crucial to configure allowed redirect URL in your Okta application profile. Such URLs should point to the /oidc path on the host addresses used by Admin Panel and Access Gateway. For example,
https://mgmt.fudo/oidc
https://10.10.0.1/oidc
https://ag.fudo/oidc
- Provide information from your Okta application profile:
- Input Client ID. This is Application (client) ID from application configuration.
- Input Client secret, which is the Client secret from application configuration.
- Input Okta domain name into the Domain field (For example,
dev-68970590.okta.com).
Note
Values for those fields come from your Okta application profile.
- Select Bind address to bind to when connecting to Okta API.
- Click .
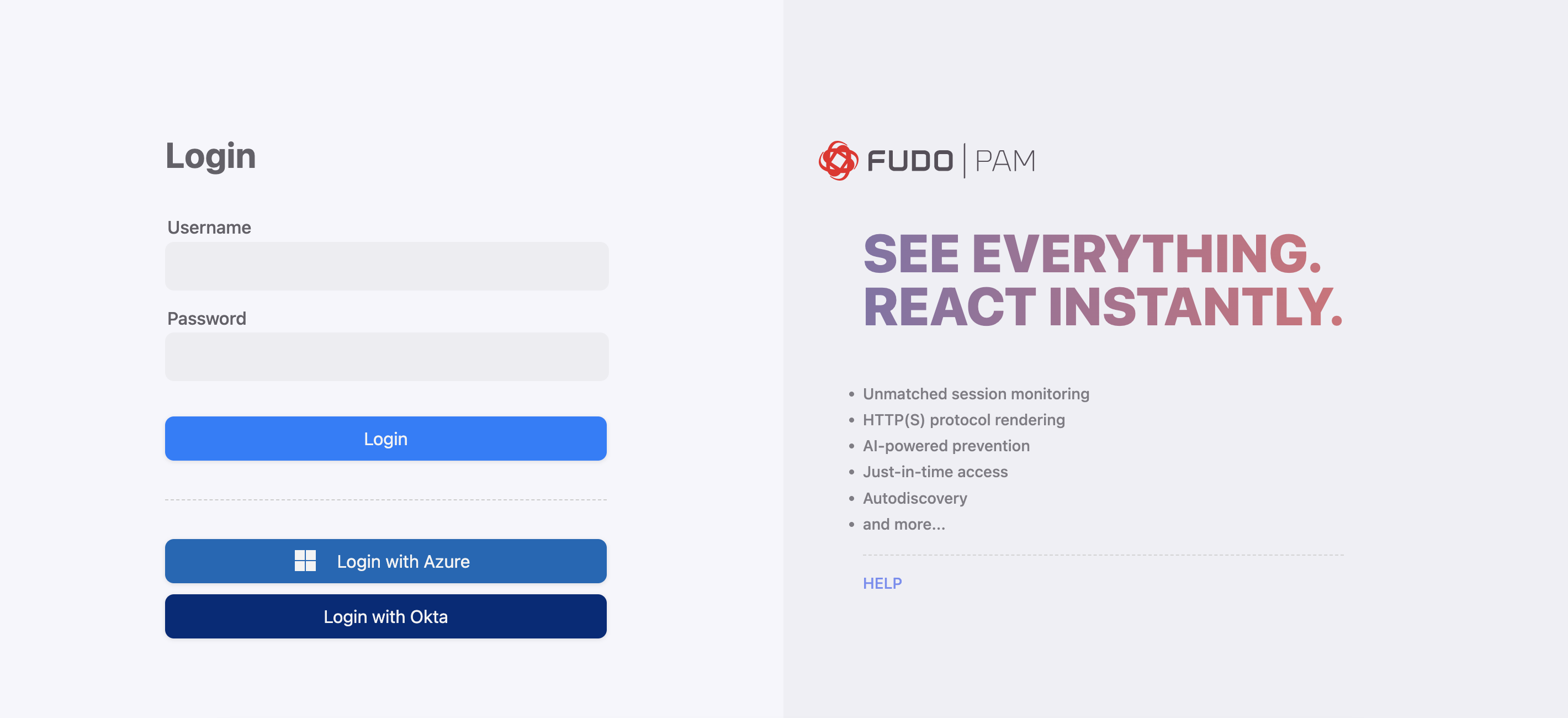
Log in using the defined authentication methods:
Related topics: