Configuration encryption¶
The Master key enables encrypting sensitive configuration parameters, system backups and external storage volumes. It also allows for recovering internal storage encryption key in case the pen drives containing encryption key are lost or damaged.
Note
- The Master key is exported to PEM format and it is encrypted with SMIME using administrator’s public key/certificate.
- It is essential to have the Master key exported and stored in a safe location.
- In case the Master key has been compromised, you can invalidate it, which will result in generating a new one and re-encrypting the data.
Exporting master key
- Select > .
- In the Maintenance and supervision click and save the file on the file system.
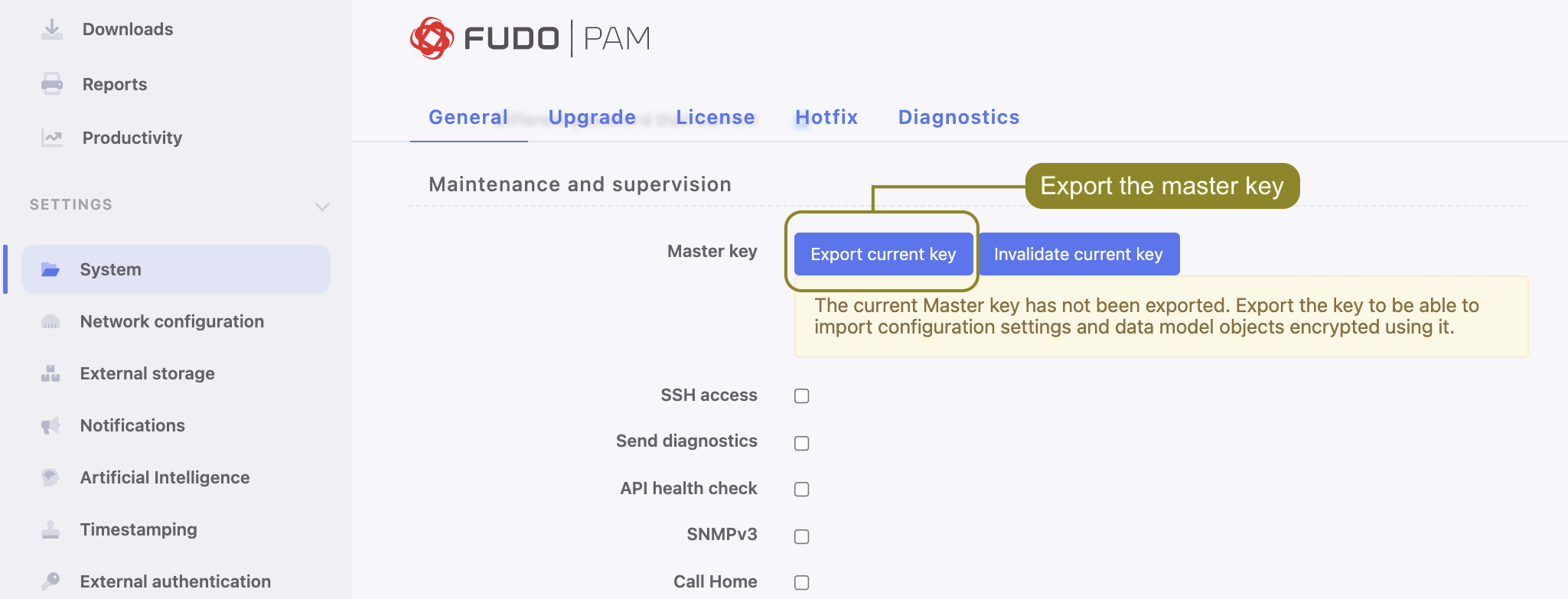
- Click and browse the file system to find the certificate that will be used to encrypt the Master key.
Note
- Generate the keys and the CSR (Certificate Signing Request) using openssl:
openssl req -newkey rsa:4096 -keyout privkey.pem -out req.pem
openssl req -nodes -newkey rsa:4096 -keyout privkey.pem -out req.pem # Do not prompt for a password.
- Sign the CSR:
openssl x509 -req -in req.pem -signkey privkey.pem -out cert.pem
- Click and save the the Master key file.
Invalidating current master key
In case the current Master key has been compromised, you can invalidate it. Invalidating the current Master key generates a new one and triggers data re-encryption.
- Select > .
- In the Maintenance and supervision click .
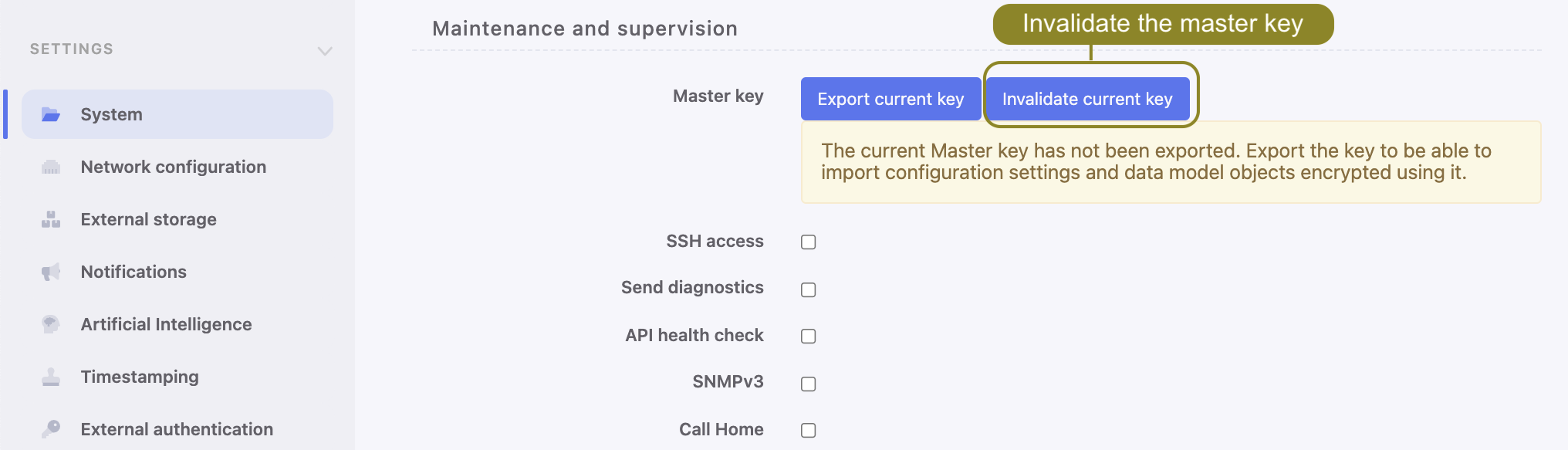
- Click to proceed with invalidating the current key and re-encrypting the data.
- Make sure to export the newly generated key.
Related topics: