Artificial Intelligence¶
Note
This is an evaluation version of the AI component.
Fudo PAM creates individual, behavioral users profiles. Based on these, it can detect even the slightest change in their behavior and prevent a security breach.
Configuring models trainers¶
Training models requires processing power. Proper system configuration enables optimal processing of archived sessions while preserving overall system responsiveness in handling current user requests.
To change models trainers configuration, proceed as follows.
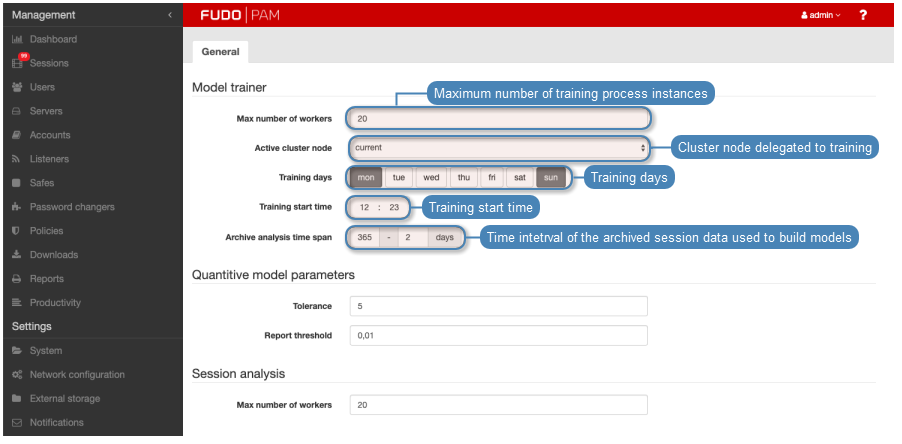
- Select > .
- In the Model trainer section, in the Max number of training instances field, define the number of processes delegated to constructing user profiles.
Note
Default value is the optimal value based on available hardware resources. The actual number of processes cannot be higher than the number of available CPU cores.
- From the Active cluster node dropdown list, select the node responsible for training models.
- Select weekdays when the training will take place.
- Set the training start time.
- Define the timespan of the data which will be processed to create models.
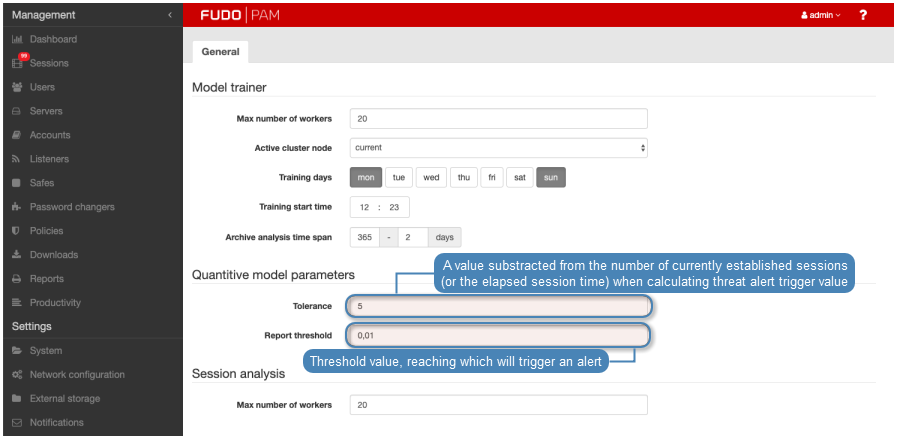
- In the Quantitive model parameters section, in the Tolerance field, define allowed delta regarding the number of connections or the length of a single session.
Note
This parameter is used to calculate the threat risk which triggers the alert. Tolerance value is deducted from the current connections number or the number of minutes of elapsed session time. E.g. if the expected number of connections is 100, the current connection number is 109 and the tolerance value is set to 10, alarm will not be triggered as the calculated value (99) is less than the expected value.
- In the Report threshold field, define the allowed deviation from the expected results.
Note
Report threshold is defined in % and it determines the threshold value when the alert gets triggered on the account of too many sessions or a single connection lasting longer than expected. E.g. with the report threshold set to 1%, the alert will be triggered if the current number of connections has been observed before in 1% of cases.
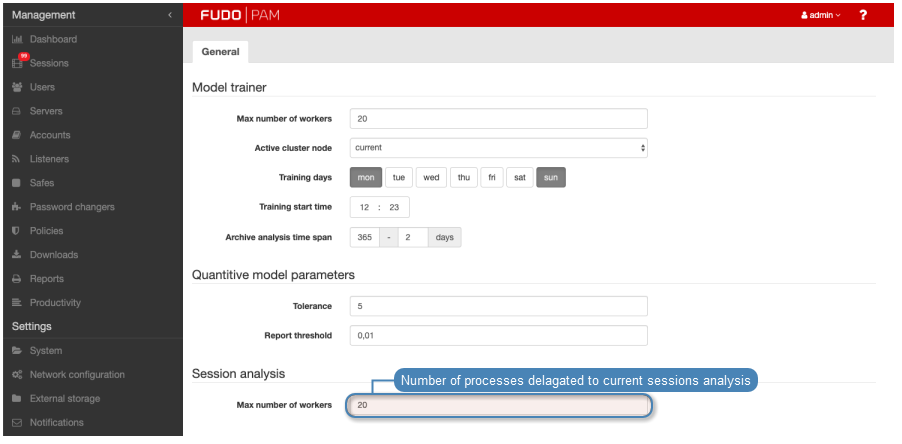
- In the Session analysis section, in the Number of analyzing instances, define the number of processes delegated to session analysis.
Note
In case the pool of available data processing processes has been exhausted, online analysis is suspended. After the session is finished the data is picked up by the session analysis processes.
- Click .
Configuring behavioral analysis models¶
Configuration parameters enable fine tuning behavioral models to match the specifics of your IT environment.
SSH
To change SSH model configuration, proceed as follows.
- Select > .
- Switch to the Models tab.
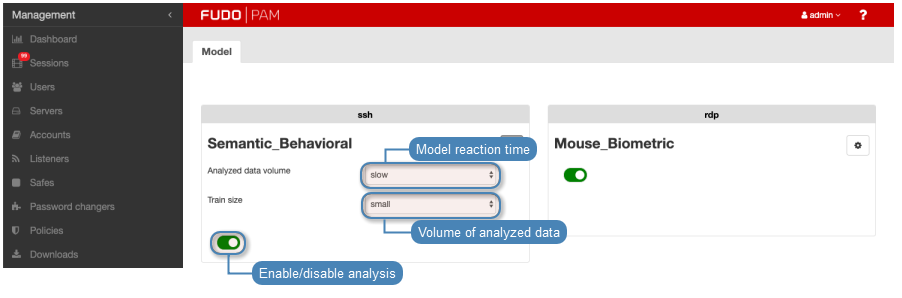
- Click the . icon for the SSH model to display related configuration parameters.
- From the Reaction time drop-down list, select how fast the system should react to delivered analysis results.
Note
Faster reaction time can potentially result in errors due to a smaller data sample.
- From the Analyzed data volume drop-down list, select how much data will be used to build the model.
- Click .
RDP
To change RDP model configuration, proceed as follows.
- Select > .
- Switch to the Models tab.
- Click the . icon for the RDP model to display related configuration parameters.
- From the Reaction time drop-down list, select how fast the system should react to delivered analysis results.
Note
Faster reaction time can potentially result in errors due to a smaller data sample.
- From the Analyzed data volume drop-down list, select how much data will be used to build the model.
- From the Feature set drop-down list, select how much features should be analyzed.
Note
Feature set determines the collection of features being analyzed. It directly influences the accuracy and the time it takes to construct the model. Analyzing extended feature set will result in a more detailed model but it will take longer to build it.
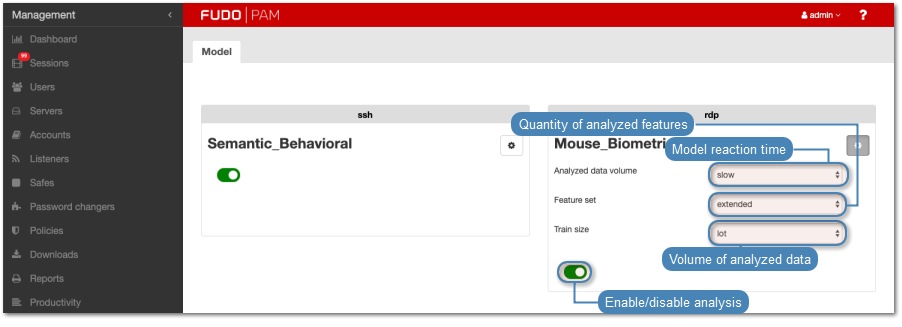
- Click .
Related topics: