AI sessions processing¶
Note
This is an evaluation version of the AI component.
Fudo PAM is able to detect changes in user behavior and determine if user credentials have been compromised. It can also alert system administrator if there is an unusually high number of connections or a particular session is longer than expected.
Content models¶
Content models process and analyze RDP and SSH sessions in order to build behavioral user profiles. Based on these, Fudo PAM can detect even the slightest change in user behavior and help prevent a security breach.
RDP content model
The RDP model is based on mouse cursor movements.
The following requirements must be met in order to produce an RDP model:
Minimum:
- 5 hours of sessions recordings per predictor,
- 5 unique predictors (e.g. users).
Optimal:
- 30 hours of sessions recordings,
- 10 unique predictors.
Note
RDP model’s quality depends on the consistency of how the user interacts with the monitored system. If the user has used different operating systems and input devices (e.g. different mice, a trackpad or a trackball) the resulting model will not be very effective as it will have a higher tolerance for a variety of behaviors.
SSH content model
The SSH content model is based on the keyboard input (commands).
The following requirements must be met in order to produce an SSH model:
Minimum:
- 65 sessions recorded (25 unique commands minimum),
- 5 unique predictors (e.g. users).
Optimal:
- 300 sessions recorded per predictor,
- 10 unique predictors (e.g. users).
Session scoring¶
Fudo PAM analyzes sessions in real-time and produces threat level scores (OK, LOW, HIGH) depending on how the user fares against the trained model.
Note
Sessions are processed in chunks containing a specific number of events. Processing is done in real-time as long as there are workers available. When there are no workers available, ongoing sessions’ parts are not analyzed.
Models are calibrated individually and session scores are presented on the session list.
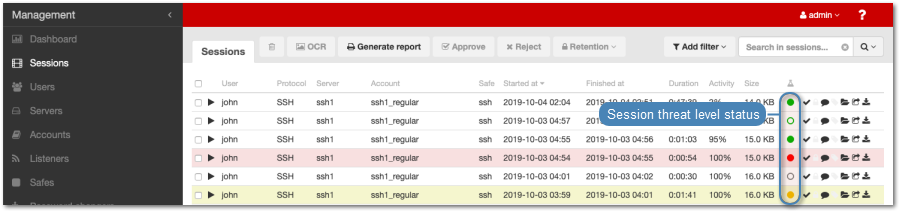
| Icon | Description |
|---|---|
| . | Session under analysis, initial result - no threat. |
| . | Session under analysis, initial result - medium threat level. |
| . | Session under analysis, initial result - high threat level. |
| . | Session awaiting analysis or being initially processed. |
| . | Session not analyzed due to missing a trained model. |
| . | Session processed - no risk. |
| . | Session processed - medium threat level. |
| . | Session processed - high threat level. |
| . | Session processed - no result. |
Note
When it comes to building user models, data quality is essential. If users shared login credentials, the resulting model will be less likely to detect the variance in user behavior.
Quantitive models¶
Fudo keeps track of the number of sessions as well as their length. It can alert system administrator if there’s an unusually high number of connections or a particular session is suspiciously long.
It does so by learning typical values for each user, account and server and making predictions for every hour and weekday.
Related topics: