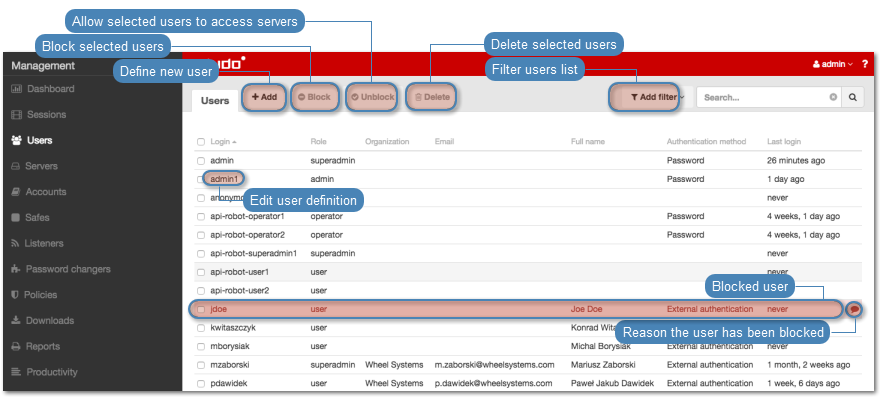
Users¶
User defines a subject entitled to connect to servers within monitored IT infrastructure. Detailed object definition (i.e. unique login, full name, email address etc.) enables precise accountability of user actions when login and password are substituted with a shared account login credentials.
Note
Wheel Fudo PAM allows importing users definitions from directory services such as Active Directory or LDAP. For more information on users synchronization service, refer to the Users synchronization topic.
Adding a user¶
Warning
Data model objects: safes, users, servers, accounts and listeners are replicated within the cluster and object instances must not be added on each node. In case the replication mechanism fails to copy objects to other nodes, contact technical support department.
- Select > .
- Click .
Note
Wheel Fudo PAM enables creating users based on the existing definitions. Click desired user to access its configuration parameters and click Copy user to create a new object based on the selected definition.
- Define configuration parameters.
| Parameter | Description |
|---|---|
| General | |
| ID | User unique identifier (applicable only when editing an existing object). |
| Synchronize with LDAP | Synchronize given user with LDAP service (applicable only when editing an existing object). |
| Login | Unique user login. |
| Blocked | Select to disable access to monitored servers. |
| Account validity | Define account validity period. |
| Role | Select role determining user access rights. |
| Preferred language | Select user’s preferred language. |
| Safes | Select safes to grant access to monitored servers. Note
|
| Full name | User’s full name for identification purposes. |
| User’s email address. | |
| Organization | Organization assignment. |
| Phone | Optional contact information. |
| AD domain | Active Directory domain to which the user is assigned to. |
| LDAP base | LDAP base to locate user in the directory service. |
| Permissions | |
| Granted users | Users allowed to manage given object. |
| Authentication | |
| Type | Select user authentication method. |
Password |
|
| Password | Provide static password. |
| Repeat password | |
| Delete | Select to delete given authenticaiton method. |
External authentication |
|
| External authentication source | Select external authentication source used to verify user’s credentials. |
SSH Key |
|
| Public key | Paste or upload user’s public key. |
- Click to define an additional authentication procedure.
- Define time access policy.
- Click desired safe object.
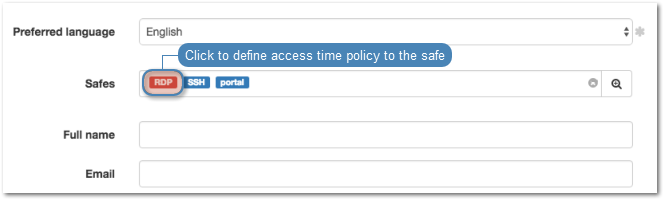
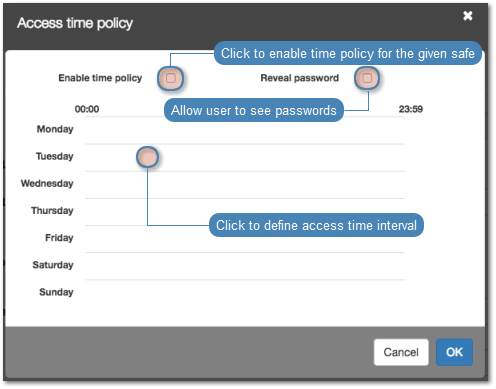
- Select Enable time policy option to apply access time policy to selected safe.
- Select Reveal password option to allow user to see passwords in the user portal.
- Click the weekly calendar to define time interval.
- Click .
- Click .
Editing a user¶
- Select > .
- Find desired user definition.
- Click user’s login to access its configuration parameters.
- Modify configuration parameters as desired.
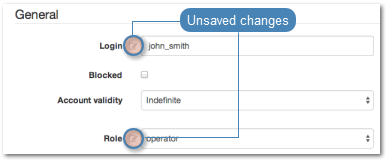
Note
Unsaved changes are marked with an icon.
- Click .
Blocking and unblocking a user
Warning
Blocking a user will terminate its current connections.
- Select > .
- Find and select the desired user definition.
- Click to disallow the user to connect to servers or to allow user to connect to servers.
- Provide a descriptive reason for blocking the given user and click .
Deleting a user¶
Warning
Deleting a user definition will terminate its current connections.
- Select > .
- Find and select the desired user definition.
- Click .
- Confirm resource deletion.
Roles¶
| Role | Access rights |
|---|---|
| user | Connecting to servers as defined in connections, to which the user has been assigned. |
| operator |
|
| admin |
|
| superadmin |
|
Related topics: